Microsoft Edge and Google Chrome will tighten local network access starting with version 141. When enforcement begins, users accessing the OneDrive Web App and integrated Microsoft 365 experiences (such as Microsoft Lists in OneDrive, SharePoint Lists, and document libraries) will encounter a browser permission prompt for local network access unless a policy is in place.
If permission is denied, performance optimizations and offline capabilities powered by OneDrive and SharePoint will not be available.
This change affects Windows, macOS, and VDI endpoints managed by enterprise policies.
Content
Timeline
- Stable release of Google Chrome 141, expected at the end of September 2025.
- Stable release of Microsoft Edge 143, expected at the beginning of December 2025.
What is changing?
After the release of Chromium 141, users will see a new browser prompt requesting permission for local network access when opening the OneDrive Web App, Microsoft Lists in OneDrive, Lists on a SharePoint site, and SharePoint document libraries.
Google explains this change on their developer blog for Chrome 141 Beta.
Local network access restrictions
Chrome 141 restricts the ability to make requests to the user’s local network, gated behind a permission prompt.A local network request is any request from a public website to a local IP address or loopback, or from a local website (for example, an intranet) to loopback. Requiring permission for websites to perform these requests mitigates the risk of cross-site request forgery attacks against local network devices such as routers, and it reduces the ability of sites to use these requests to fingerprint the user’s local network.
This permission is restricted to secure contexts. If granted, the permission additionally relaxes mixed content blocking for local network requests (since many local devices are not able to obtain publicly trusted TLS certificates for various reasons).
This work supersedes an earlier effort called “Private Network Access”.
I installed Edge 141 Beta and Chrome 141 Beta to simulate the case.
Edge 141 Beta (Version 141.0.3537.13 Beta) is not yet ready for testing, as the new permission is currently disabled by default. Chrome 141 Beta (Version 141.0.7390.16 Beta) is ready.
***************
Updated 4 October 2025:
Google Chrome 141 was released on 29 September. OneDrive and SharePoint will notify users that performance optimizations may be affected if the local network access policy is not configured.
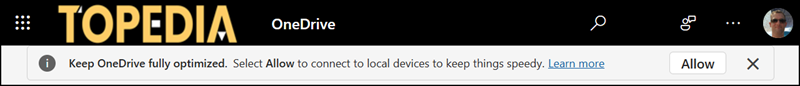
Microsoft informed that the new local network access permission is included in Edge 141 but is still disabled by default; it will be enabled with Edge 143. The stable channel release of Edge 143 is scheduled for calendar week 49/2025 (1 – 7 December).
Local Network Access
Local Network Access in Microsoft Edge is a security feature that restricts a website’s ability to send requests to servers on your local network. When a website tries to connect, Microsoft Edge shows a prompt asking you to grant or deny permission. This protects privacy and security while maintaining compatibility with modern web standards. The ability of a website to request this permission from users is restricted to secure contexts. This feature is currently disabled by default in Microsoft Edge, but the default state will change starting in Edge 143. Enterprise administrators can configure Local Network Access policies.
***************
Users will see the new prompt…
- In OneDrive
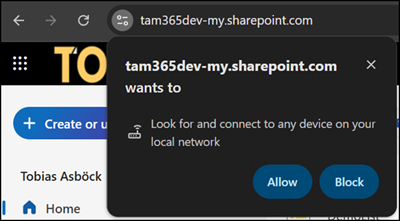
- In SharePoint Lists (check the Lists endpoint in the URL, the same for Microsoft Lists in OneDrive):
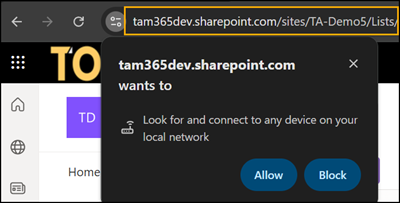
- Then users will also find a new local network access permission in the browser.
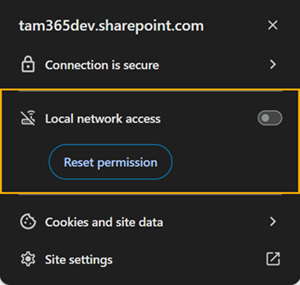
- And a new local network access permission section for the site is available, with the default value set to Ask. This section is not yet available in Edge 141 Beta.
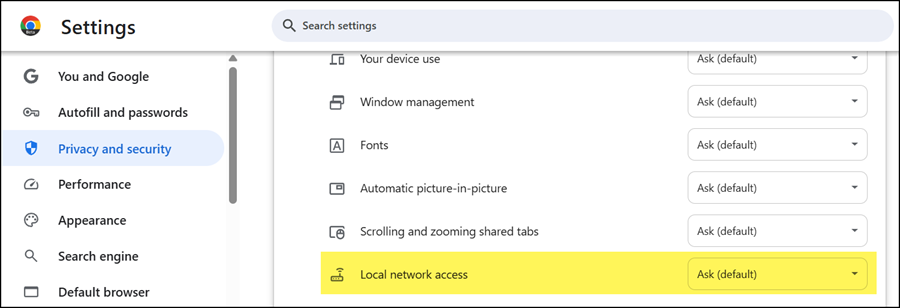
What is the impact?
If users select Block, performance optimizations and offline capabilities powered by OneDrive Web and SharePoint Web will not be available.
- This prompt does not impact offline sync in OneDrive, SharePoint, or OneDrive Shortcuts.
- This prompt impacts Offline mode in the OneDrive Web app.
- Microsoft first announced Offline mode in OneDrive Web in October 2022 and reiterated it in April 2024 (see the blog post).
Do not be surprised if you still miss offline mode. This feature has some limitations. If you do not yet have the feature in your OneDrive, review the limitations at the end of the support article.
For example:
Currently, offline mode is not supported if you have an active shortcut to shared folders in OneDrive, or if you had a shortcut in the past and later removed it. We are actively working to address this limitation.
How to prepare for Chromium 141?
Admins should configure the LocalNetworkAccessAllowedForUrls policy in Microsoft Edge and Google Chrome. This policy is already available in Chromium 140.
Define your tenant URLs and any alternatives used by your organization (such as Intranet URLs).
- https://YOURTENANT-my.sharepoint.com
- https://YOURTENANT.sharepoint.com
- + Alternatives if used by your organization
***************
Updated 29 November 2025:
Microsoft now recommends adding the following eCDN URLs to your Local Network Access policy.
The LocalNetworkAccessAllowedForUrls policy allows specific websites to access resources on local network endpoints, which is essential for Microsoft eCDN’s peer-to-peer functionality. Without this policy configuration, browser-based clients may be prevented from establishing peer-to-peer connections within your organizational network.
You should add these URLs to your policy.
- [*.]ecdn.teams.microsoft.com
- [*.]ecdn.teams.cloud.microsoft
- https://teams.microsoft.com
- https://teams.cloud.microsoft
- https://engage.cloud.microsoft
***************
In my case, I could not find the Google Chrome configuration of LocalNetworkAccessAllowedForUrls in Intune (the Edge configuration is available), so I deployed a PowerShell script via Intune to create the required registry keys. You can use the Intune Settings Catalog to deploy the URLs if you just use Microsoft Edge in your organization.
# Deploy the script via Intune to set registry keys for Local Network Access in Chrome and Edge
$TenantName = "<TenantName>" # Replace it with your tenant
# Define registry path and values
$ChromeRegistryPath = "HKLM:\SOFTWARE\Policies\Google\Chrome\LocalNetworkAccessAllowedForUrls"
$EdgeRegistryPath = "HKLM:\SOFTWARE\Policies\Microsoft\Edge\LocalNetworkAccessAllowedForUrls"
$LNAName1 = "1" # Do not change this number, as it must be a number like 1, 2, 3,.... You can add more entries by incrementing this number.
$LNAValueUrl1 = "https://$TenantName.sharepoint.com"
$LNAName2 = "2" # Do not change this number, as it must be a number like 1, 2, 3,.... You can add more entries by incrementing this number.
$LNAValueUrl2 = "https://$TenantName-my.sharepoint.com"
# Create the registry path if it does not exist
if (-not (Test-Path $ChromeRegistryPath)) {
New-Item -Path $ChromeRegistryPath -Force | Out-Null
}
if (-not (Test-Path $EdgeRegistryPath)) {
New-Item -Path $EdgeRegistryPath -Force | Out-Null
}
# Set the registry values for Google Chrome and Microsoft Edge
New-ItemProperty -Path $ChromeRegistryPath -Name $LNAName1 -Value $LNAValueUrl1 -PropertyType String -Force | Out-Null
New-ItemProperty -Path $ChromeRegistryPath -Name $LNAName2 -Value $LNAValueUrl2 -PropertyType String -Force | Out-Null
New-ItemProperty -Path $EdgeRegistryPath -Name $LNAName1 -Value $LNAValueUrl1 -PropertyType String -Force | Out-Null
New-ItemProperty -Path $EdgeRegistryPath -Name $LNAName2 -Value $LNAValueUrl2 -PropertyType String -Force | Out-Null
The registry keys were created after a reboot of my client. Google Chrome confirmed the policy is in place.
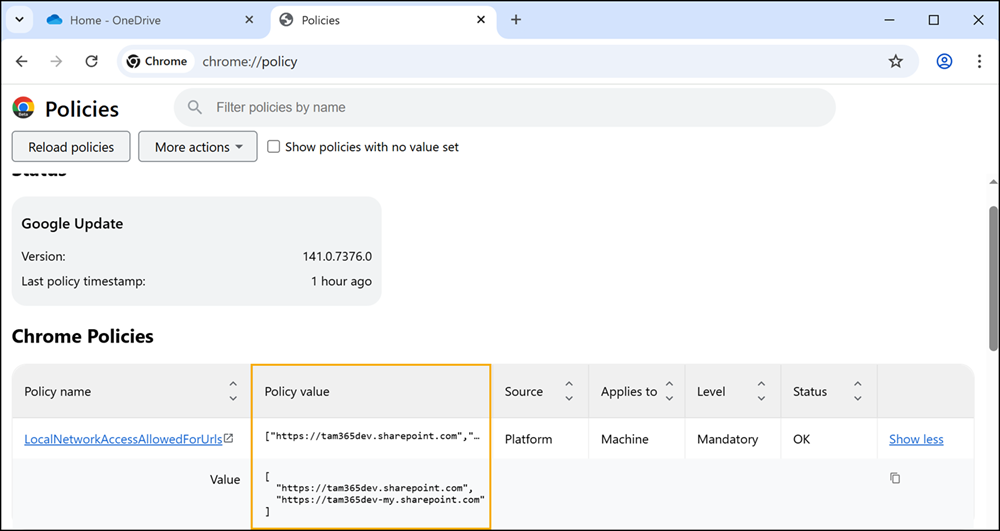
The new local network access permission is now defined as Allow for my two predefined SharePoint URLs, and users cannot change it.
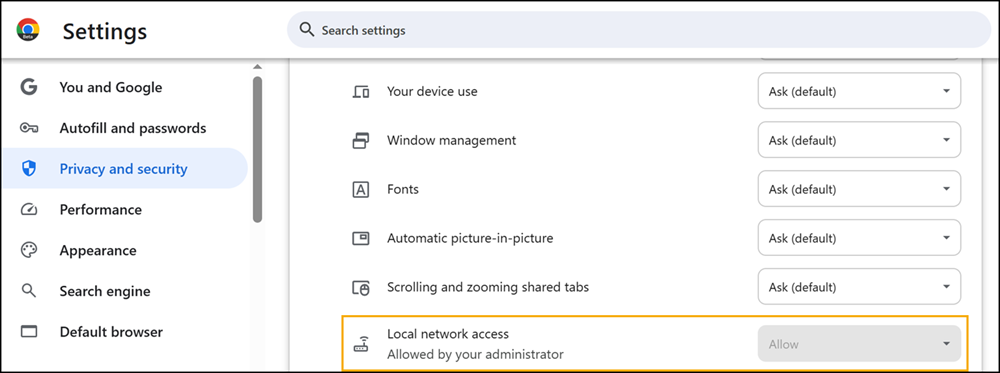
The same policy is in place for Microsoft Edge.
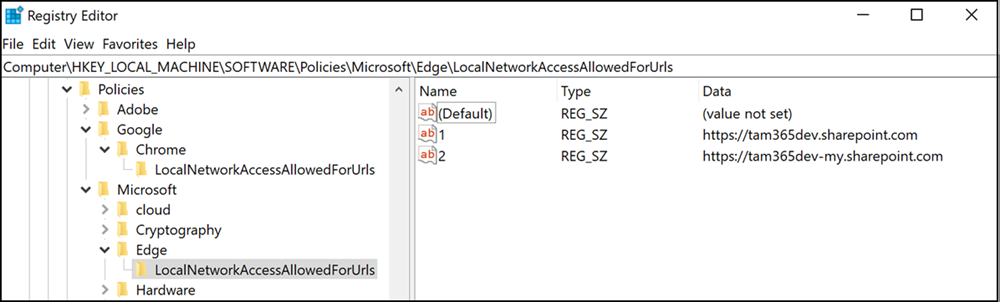
Congratulations, you are now covered for Chromium 141.
Note:
Applying the managed LocalNetworkAccessAllowedForUrls policy overrides prior per-user deny states and enforces allow once the policy is active. No end-user action is required after policy propagation.

Can we add registry keys with wildcard characters, just to match the subdomain or domain?
Hello Elton, yes, that’s possible. You can check Microsoft’s sample here. For example, you could add
https://*.YourDomain.comas record 1, and it should apply to all your internal subdomains. Microsoft recommends keeping wildcard configurations as strict as possible.