Microsoft has introduced new Trust Center controls in Microsoft 365 Apps for Windows to reduce exposure to legacy protocols.
Starting with version 2508:
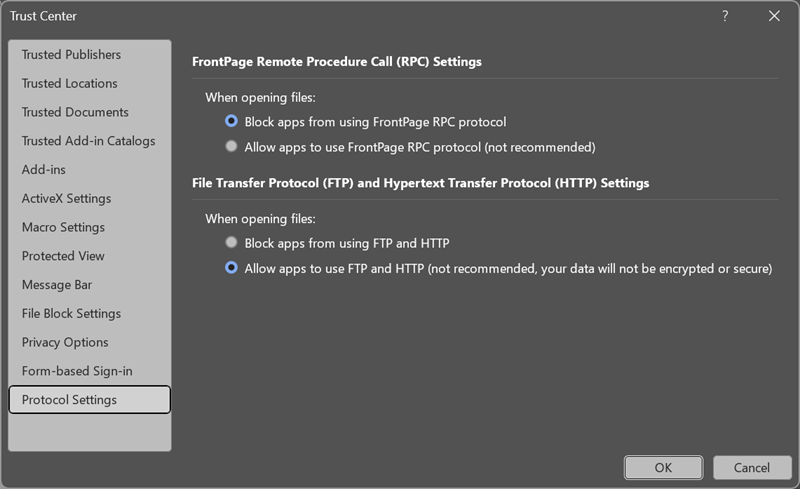
- File opens using FrontPage Remote Procedure Call (FPRPC) are blocked by default, with a more secure fallback protocol used when available.
- New Trust Center settings allow users to disable FTP and HTTP file opens. By default, these protocols remain allowed unless changed by an admin.
Timeline
The new Trust Center controls are available in Microsoft 365 Apps for Windows starting with version 2508.
This update does not affect Microsoft 365 apps on macOS, Microsoft Teams, the web, or mobile.
How does this affect your users?
Legacy protocols such as FrontPage Remote Procedure Call (FPRPC) are now blocked by default, though admins can change this behavior using Group Policy or Cloud Policy service. Other legacy protocols, including FTP and HTTP in apps, remain allowed by default, but users and admins can modify these settings.
Admin controls and configuration
Admins can configure these new protocol settings through either Group Policy or the Cloud Policy service.
If you’re using the Group Policy Management tool, all these policy settings are located under User Configuration\Policies\Administrative Templates\Microsoft Office 2016\Privacy\Trust Center.
The following policies are available in the Cloud Policy service:
Restrict Apps from FPRPC Fallback
This policy setting allows you to control the fallback behavior of Microsoft 365 apps when using FrontPage Server Extensions Remote Procedure Call Protocol (FPRPC).
- If you enable this policy setting, Microsoft 365 apps will not use FPRPC.
- If you disable this policy setting, Microsoft 365 apps will continue to use FPRPC.
- If you don’t configure this policy setting, Microsoft 365 apps will continue to use FPRPC.
Block Insecure Protocols
This policy setting allows you to control which protocols can be used when opening documents in Microsoft 365 apps.
- If you enable this policy setting, non-HTTPS links will be blocked when opening documents in Microsoft 365 apps.
- If you disable this policy setting, all protocols and links will be allowed when opening documents in Microsoft 365 apps.
- If you don’t configure this policy setting, all protocols and links will be allowed when opening documents in Microsoft 365 apps.
