Microsoft is introducing a new capability in Teams external collaboration that allows administrators to assign external domain access policies to specific users or Microsoft Entra ID groups. Previously, external domain access was limited to an organization-wide control.
This new capability enables precise control over which external domains each audience can interact with, supporting scenarios such as pilot rollouts with selected departments, restrictions for high-risk roles, or broad federation for trusted groups.
Timeline
The rollout should be completed by December 2025.
What is changing
External domain access settings in Teams were previously limited to organization-wide control, with policy-level options to either inherit tenant settings or block all external domains.
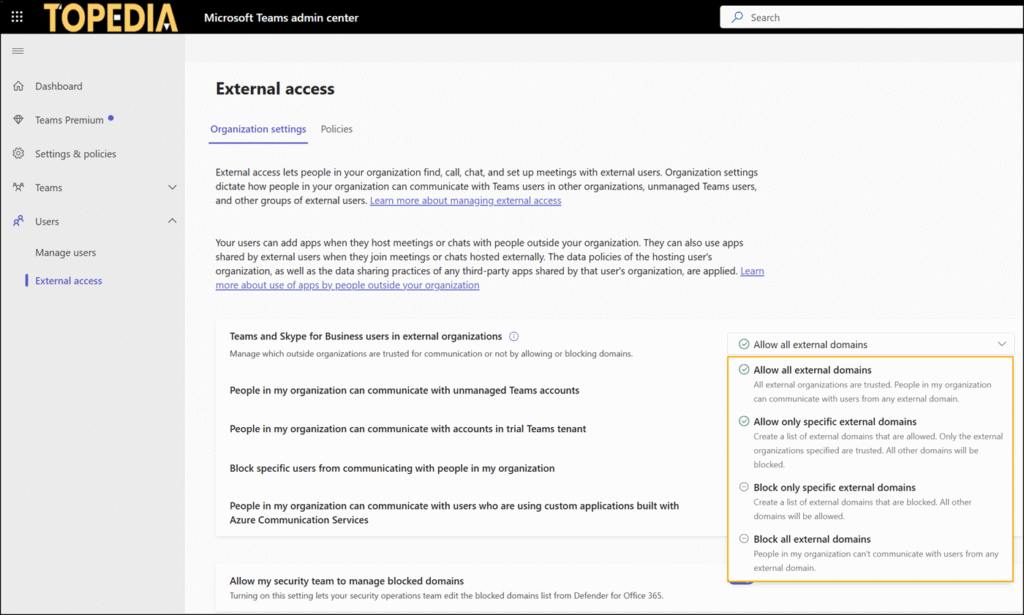
The new capability introduces custom external domain access policies that can be assigned to user accounts or Entra ID groups. Each policy offers five configurations, enabling granular external collaboration controls for different scenarios such as pilots, restricted roles, or broad federation setups.
- OrganizationDefault: Inherits the tenant’s default external access configuration.
- AllowAllExternalDomains: All external organizations are trusted.
- AllowSpecificExternalDomains: Only domains in the allow list are trusted.
- BlockSpecificExternalDomains: Domains in the block list are restricted; all others are trusted.
- BlockAllExternalDomains: All external domains are blocked for users assigned to this policy.
If you check your external access policies, you will notice the following properties are now configurable:
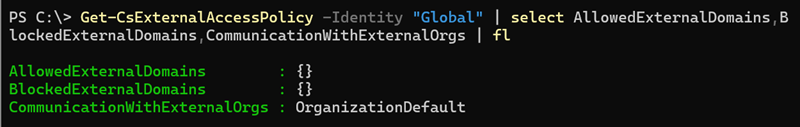
Microsoft notes the three properties are currently in Public Preview. If the rollout in your tenant has not yet been completed, you will receive an error message like this:
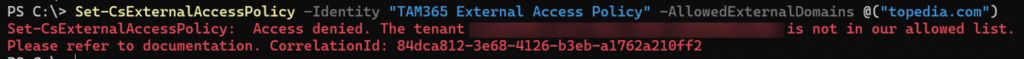
Once the rollout is completed, you can configure these properties using PowerShell. Configuration in the Teams Admin Center is not yet available. I created a new custom policy for my scenario.
It’s important to update CommunicationWithExternalOrgs with the correct value to reflect your changes; otherwise, the policy may continue using the organization’s default configuration.
Set-CsExternalAccessPolicy -Identity "Topedia External Access Policy" -AllowedExternalDomains @("demo1.tam365.com") -CommunicationWithExternalOrgs "AllowSpecificExternalDomains"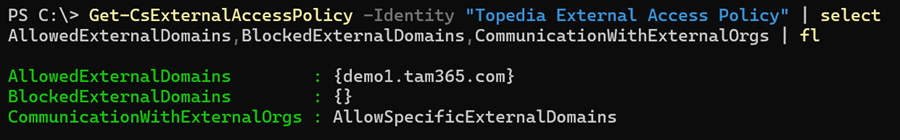
Next, you can assign the policy to an Entra ID group or individual user accounts.
# Group policy assignment
Grant-CsExternalAccessPolicy -PolicyName "<PolicyName>" -Group "<GroupID>" -Rank 1
# User policy assignment
Grant-CsExternalAccessPolicy -PolicyName "<PolicyName>" -Identity "<UserPrincipalName>"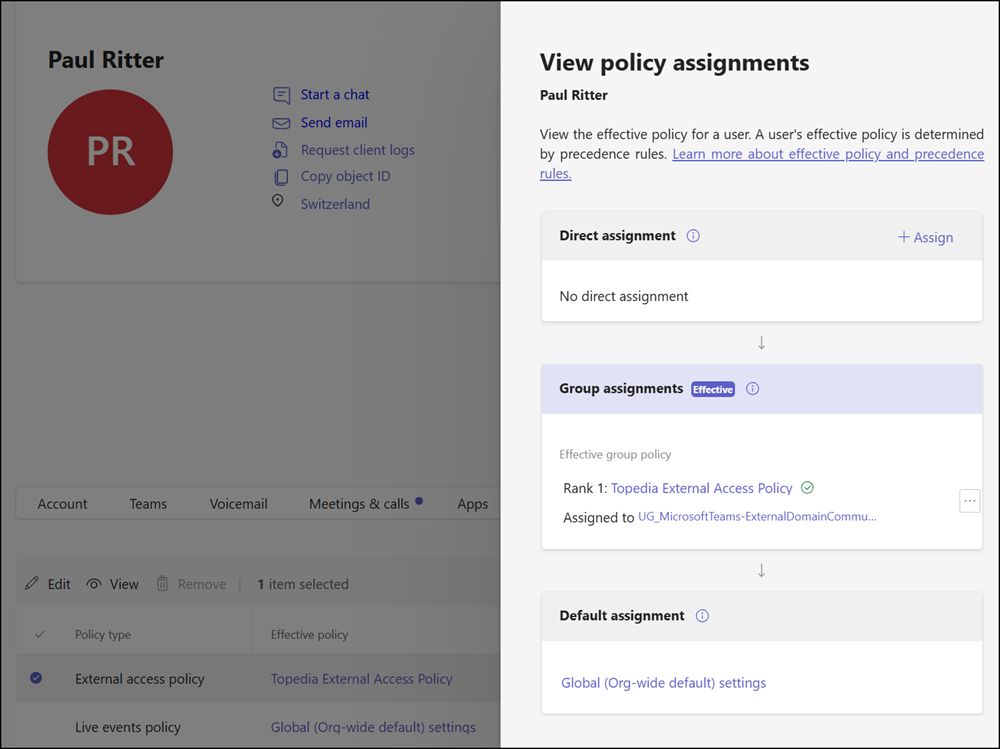
Now, members of the assigned group can communicate with my Dev-tenant, while all other external domains are blocked. Users who are not part of the group continue to follow the organization-wide policy.
Now you have to keep in mind:
Users assigned a custom external access policy may be able to communicate with different external domains than those defined in the organization-wide configuration.
