Microsoft Teams now integrates with Microsoft Defender for Office 365, allowing security admins to manage blocked domains for Teams using the Tenant Allow/Block List in the Microsoft Defender portal. This integration centralizes domain blocking across Microsoft 365 services and applies to all Teams clients as well as the Defender XDR portal.
Timeline
The rollout should be completed in September 2025.
Updated 22 November 2025:
The rollout should be completed by the end of January 2026.
Impact for your organization
Teams admins can now enable a new option under Users > External Access to apply blocked domains from the Microsoft Defender Tenant Allow/Block List.
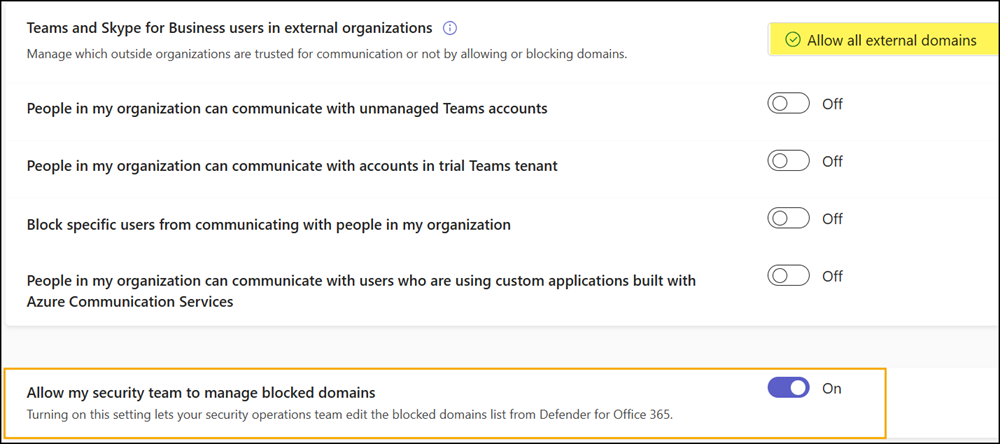
Admins can also configure this setting using PowerShell with the DomainBlockingForMDOAdminsInTeams property.
DomainBlockingForMDOAdminsInTeams
When set to ‘Enabled’, security operations team will be able to add domains to the blocklist on security portal. When set to ‘Disabled’, security operations team will not have permissions to update the domains blocklist.
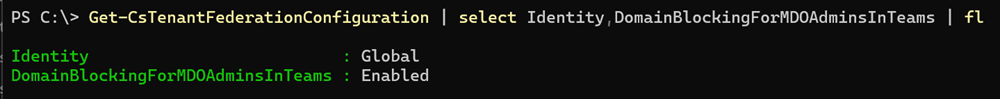
This option is disabled by default and must be explicitly enabled to grant security administrators access to manage blocked domains for Teams. Teams supports up to 4,000 blocked domains.
Security admins find a new option to block Teams domains in the Tenant Allow/Block list.
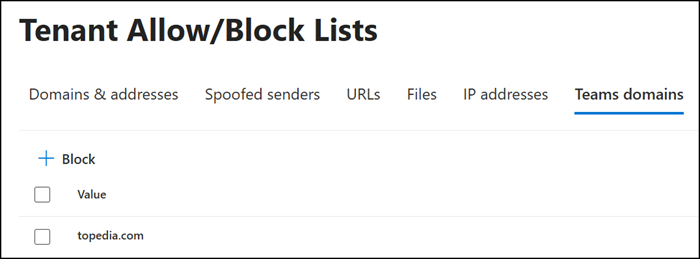
If a blocked domain is added, Defender will update the external access configuration to “Block only specific external domains.”
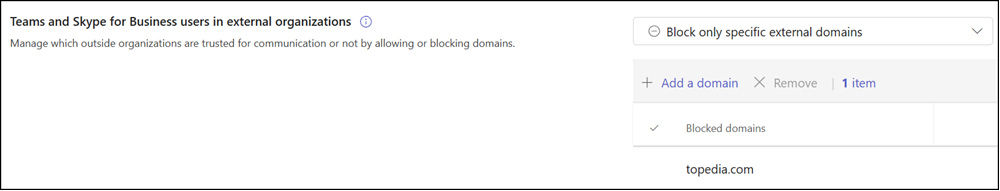
Incoming communications from blocked domains are prevented across chats, channels, meetings, and calls. As Microsoft states, existing communications from these domains can be automatically deleted. Actions taken to block domains are recorded in audit logs for compliance monitoring and reporting purposes.
This change does not affect existing federation configurations or domain blocks set directly in the Teams admin center.
As outlined in the documentation, three prerequisites apply:
- A Microsoft Defender for Office 365 Plan 1 or Plan 2 is required.
- A Teams admin must enable the option to manage blocked domains via Microsoft Defender.
- A Teams admin must configure external access as either “Block only specific external domains” or “Allow all external domains”.
