Microsoft is rolling out three new security features for Teams chats and channel conversations.
- Weaponizable File Protection
- Malicious URL Protection
- Report as not a security concern
These new features are designed to warn both the sender and recipient before risky actions occur, and to allow internal users to report false/positives without raising a support ticket.
Content
Timeline
- Public Preview
Rollout should be completed in September 2025. Features are disabled by default during Preview. A Teams admin must explicitly enable them. - General Availability
Rollout should be completed in November 2025. Features will be enabled by default unless an admin has changed the configuration during Preview.
What is new
Weaponizable File Protection
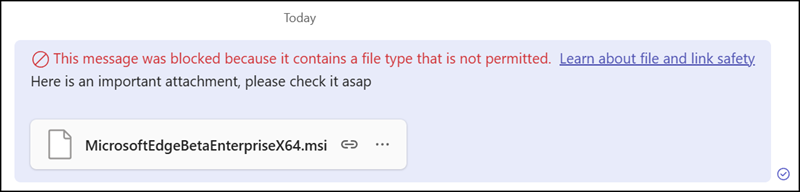
With Weaponizable File Protection, Microsoft blocks messages containing weaponizable file types (for example, executables) in chats and channels, both internal and external. The feature reduces exposure to malware and file-based attacks by preventing the sharing of unsafe content.
- Senders receive a notification and can edit and resend the message without the unsafe file.
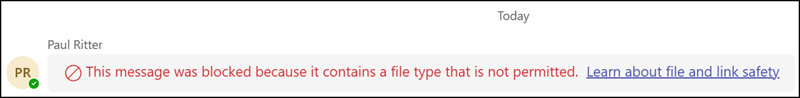
- Recipients see a notification that a message was blocked and cannot access the content.
The following file types are blocked. The list cannot be customized by admins:
ace, ani, apk, app, appx, arj, bat, cab, cmd, com, deb, dex, dll, docm, elf, exe, hta, img, iso, jar, jnlp, kext, lha, lib, library, lnk, lzh, macho, msc, msi, msix, msp, mst, pif, ppa, ppam, reg, rev, scf, scr, sct, sys, uif, vb, vbe, vbs, vxd, wsc, wsf, wsh, xll, xz, z
- Public Preview
Disabled by default until November. All participant organizations in the conversation must have the feature enabled to receive protection. - General Availability
Enabled by default unless an admin disabled it during Preview. Protection is enforced if at least one participant has the feature enabled.
The licensing requirement for Weaponizable File Protection has not yet been documented.
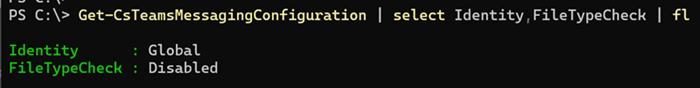
Admins can enable or disable the feature via Teams Admin Center (Messaging policy) or PowerShell using the Teams messaging configuration. It’s the property FileTypeCheck.
FileTypeCheck
This setting enables weaponizable file detection in Teams messages in the tenant.
Malicious URL Protection
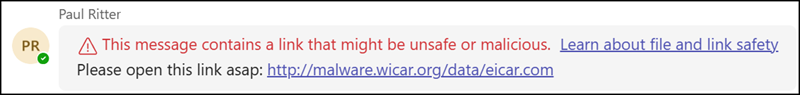
Malicious URL Protection safeguards users from harmful links shared in chats, channels, and meeting messages. Teams scans links against Defender for Office 365 threat intelligence databases. If a link is flagged, clear warnings are displayed to the sender and all recipients.
Unlike Safe Links in Teams, Malicious URL Protection does not block users from opening the link. Therefore, it is included in all Teams licenses as part of base protection.
Public Preview
Disabled by default until November. All participant organizations in the conversation must enable it for protection to apply.
General Availability
Enabled by default unless an admin disabled it during Preview. Protection is enforced if at least one participant has the feature enabled.
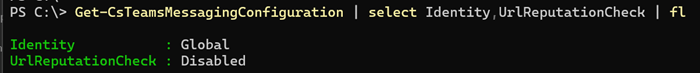
Admins can enable or disable the feature via Teams Admin Center or PowerShell. It’s the property UrlReputationCheck.
UrlReputationCheck
This setting enables malicious URL detection in Teams messages in the tenant.
Report as not a security concern
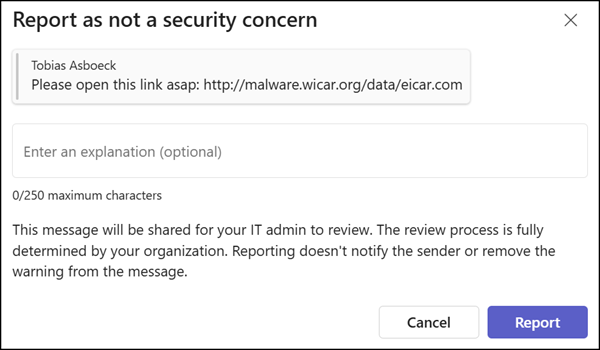
Users in Teams can report a security concern since June 2023. The new feature allows them to report messages incorrectly flagged as threats. This reduces false/positives, improves detection accuracy, and decreases support tickets.
This feature has the same licensing requirements as “Report a security concern”. Users need a Defender for Office 365 Plan 2 service plan or license.
Public Preview: Disabled by default until November.
General Availability: Enabled by default unless an admin disabled it during Preview.
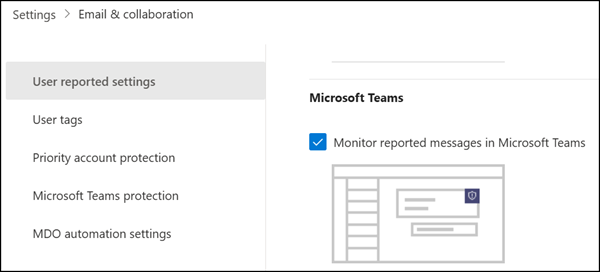
This feature also requires activation in the Microsoft Defender portal.
It is enabled by default for new tenants, but not for existing ones. Users can report false/positives if user-reported messages are enabled.
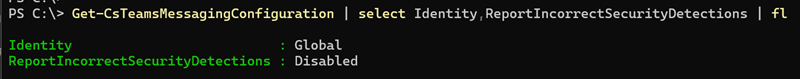
Admins can enable or disable the feature via Teams Admin Center or PowerShel. It’s the property ReportIncorrectSecurityDetections.
ReportIncorrectSecurityDetections
This setting enables end users to report incorrect security detections in Teams messages in the tenant.