Microsoft is retiring support for inline SVG images in Outlook for the web and the new Outlook for Windows. This change is designed to enhance security and align with prevailing email client behavior, where inline SVG rendering is commonly restricted.
Timeline
Retirement starts in September 2025.
How does this affect your organization?
If an email sent to Outlook contains an inline SVG image (for example, hosted on an external server), it is currently rendered for recipients using Outlook for the web or the new Outlook for Windows, which is a security risk. This update mitigates potential vulnerabilities, including cross-site scripting (XSS) vectors that can be exploited through embedded SVG content.
Two security examples:
- Pixel-Perfect Trap: The Surge of SVG-Borne Phishing Attacks
- SVG Phishing Attacks: The New Trick in the Cybercriminal’s Playbook – VIPRE
SVG (Scalable Vector Graphics) files are vector-based images commonly used for crisp logos, icons, and graphics due to their ability to scale without losing quality. Unlike typical image formats like JPEG or PNG, SVG files are based on XML (Extensible Markup Language), allowing them to contain interactive elements and scripts.
…
While SVG (Scalable Vector Graphics) files are widely used in web design and branding, their ability to embed JavaScript also introduces serious cybersecurity risks.
Cybercriminals exploit this feature by inserting malicious scripts directly into SVG files. These scripts can execute automatically upon opening the file, enabling a wide range of cyberattacks, including unauthorized system access, data theft, identity compromise, and leakage of sensitive information.
Current behavior in Outlook:
- Outlook Classic already blocks inline SVG rendering, displaying a blank placeholder.
- Outlook for the web and the new Outlook for Windows still render inline SVG images.
- Outlook Mobile still renders inline SVG images.
Microsoft states this change will affect fewer than 0.1% of all images used in Outlook.
I was curious to test this scenario myself, because I couldn’t easily insert an SVG image into an email.
The key to displaying an SVG image in Outlook is to embed it in the email’s HTML. There are even discussions online about using SVG images in Outlook signatures (like this here). If you rely on this approach, it’s time to change it.
In my test, I created a simple HTML body and sent it via Microsoft Graph. The image displayed as expected, and recipients had no indication that it was being loaded from an external source.
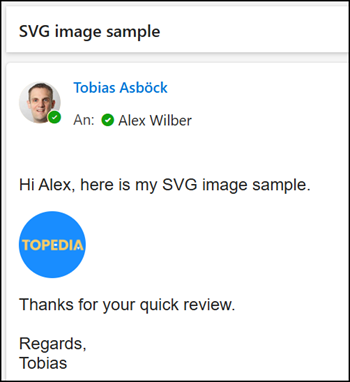
I can see the external path to the image hosted on my blog when inspecting the HTML source of the email.
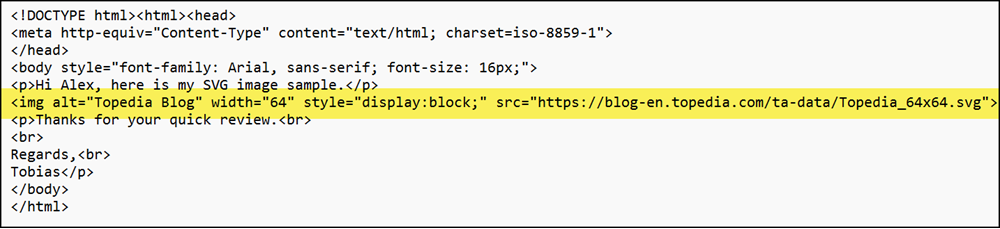
Starting in September, Outlook for the web and the new Outlook for Windows will block these images. Users will instead see a blank placeholder where the images would have appeared.
Users will still be able to add SVG images as attachments; this behavior is not changing. However, attached SVG files can also pose a security risk.
Web browsers such as Chrome, Firefox, Safari, and Edge natively handle SVG files and automatically execute embedded JavaScript without issuing security alerts. This makes SVG phishing highly effective, as users receive minimal warning about the potential risks.
In contrast, desktop email clients like Outlook and Thunderbird generally do not execute scripts within SVG files. Instead, they prompt users to open these files in an external browser, inadvertently increasing phishing risks by transferring the attack vector to a less secure environment.
