SharePoint Embedded containers used by Microsoft apps, such as Loop Workspaces, Microsoft Designer, and Outlook Newsletters, are essentially a black box for administrators. While there’s no way to configure storage settings or apply quotas, admins can still gain visibility into what’s happening inside these containers using Microsoft Purview Audit Logs.
All key activities are logged and traceable. Microsoft even highlights that SharePoint Embedded containers are integrated with Purview compliance solutions.
Since these containers are a black box for admins and lack technical documentation from Microsoft, I spent some hours investigating their behavior using Microsoft Purview.
To start your investigation, you’ll need the application ID associated with each container type.
Below is a list of Microsoft-owned applications and their corresponding IDs. While some of these IDs are not yet officially documented, they are the actual identifiers used by Microsoft’s services. Some of the containers are even hidden in the SharePoint admin center. You find them with SharePoint Online PowerShell.
| Owning Application | Application ID |
|---|---|
| Loop Workspaces | a187e399-0c36-4b98-8f04-1edc167a0996 |
| Microsoft Designer | 5e2795e3-ce8c-4cfb-b302-35fe5cd01597 |
| Outlook Newsletters | 155d75a8-799c-4ad4-ae3f-0084ccced5fa |
| Declarative Agent | e8be65d6-d430-4289-a665-51bf2a194bda |
| Teams Virtual Event VOD | 7fc21101-d09b-4343-8eb3-21187e0431a4 |
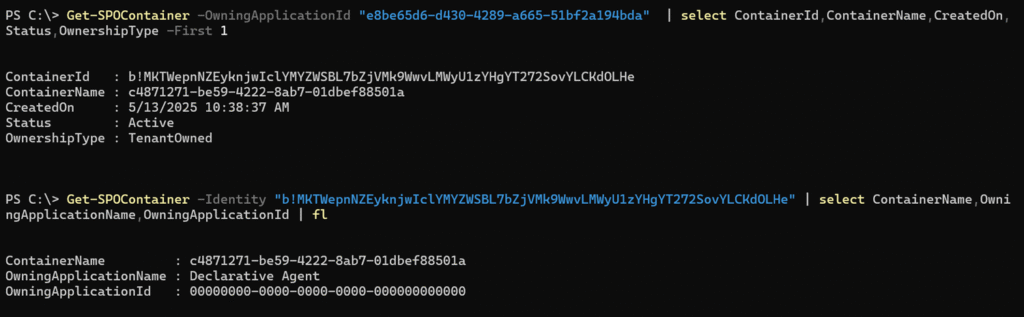
For example, I list a Declarative Agent container using SharePoint Online PowerShell. If your tenant doesn’t contain one of the containers, the PowerShell query will result in an error.
I recommend retrieving your Purview Audit Logs via Microsoft Graph, as it allows you to easily filter activities by SharePoint Embedded application ID. I outlined the process back in March 2024.
- You need to ensure your app has the correct authentication scopes to query audit logs:
- For all containers, the main required permission is AuditLogsQuery-SharePoint.Read.All.
- For Outlook Newsletters containers, you need AuditLogsQuery-SharePoint.Read.All (required) and optionally AuditLogsQuery-Exchange.Read.All if you also want to include mailbox activity.
In the example below, I’ll demonstrate how to retrieve activity logs for Outlook Newsletter containers using both SharePoint and Exchange data sources.
Import-Module Microsoft.Graph.Authentication
Connect-MgGraph -Scopes AuditLogsQuery-SharePoint.Read.All, AuditLogsQuery-Exchange.Read.All- Create a new search job for the Purview Audit Logs. Don’t worry if the initial query returns a large number of activities; we’ll apply filters during the analysis phase.
# Create a new audit log query for Outlook Newsletters covering the past 7 days
$StartDate = (Get-Date).AddDays(-7).ToString("yyyy-MM-ddT00:00:00Z")
$EndDate = (Get-Date).ToString("yyyy-MM-ddTHH:mm:ssZ")
$Body =
@"
{
"displayName": "MSGraphAuditlogQuery-OutlookNewsletters-1",
"filterStartDateTime": "$StartDate",
"filterEndDateTime": "$EndDate",
"serviceFilters": [
"SharePoint",
"Exchange"
]
}
"@
$Url = "https://graph.microsoft.com/beta/security/auditLog/queries"
$AuditLogNewQuery = Invoke-MgGraphRequest -Method POST -Uri $Url -Body $Body -ContentType "application/json"
$AuditLogNewQuery- Wait until the search job has completed.
# Get the status of the new search job
$AuditLogNewQueryID = $AuditLogNewQuery.id
$Url = "https://graph.microsoft.com/beta/security/auditLog/queries/$AuditLogNewQueryID"
$AuditLogNewQueryResult = Invoke-MgGraphRequest -Method Get -Uri $Url -ContentType "application/json"
$AuditLogNewQueryResult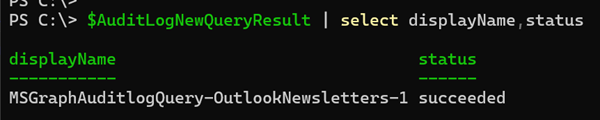
- Get the results. My sample handles paging, ensuring you retrieve all available records.
# Get the results of the search job (paging included)
$Url = "https://graph.microsoft.com/beta/security/auditLog/queries/$AuditLogNewQueryID/records?`$top=1000"
$AuditLogNewQueryResultRecords = @()
While ( $null -ne $Url ) {
$data = Invoke-MgGraphRequest -Method GET -Uri $Url -ContentType "application/json"
$AuditLogNewQueryResultRecords += $data.Value
$Url = $data.'@Odata.NextLink'
}- Filter your results by application ID, in my case, 155d75a8-799c-4ad4-ae3f-0084ccced5fa, which represents activities related to Outlook Newsletter containers. These activities are initiated by the container application and should give you insight into the actions performed by the application.
$OutlookNewsletterEvents = $AuditLogNewQueryResultRecords | ?{$_.auditData.ApplicationId -eq "155d75a8-799c-4ad4-ae3f-0084ccced5fa" }
You now have all results from the last seven days; in my case, 407 activities.
Filtering with PowerShell is now straightforward.
First, take a look at what’s included in the results. Start by inspecting a random activity.
$OutlookNewsletterEvents[10].auditData | select ApplicationDisplayName,ApplicationId,ContainerInstanceId,ItemType,Operation,SourceFileName,CreationTime,FileSizeBytes,SiteUrl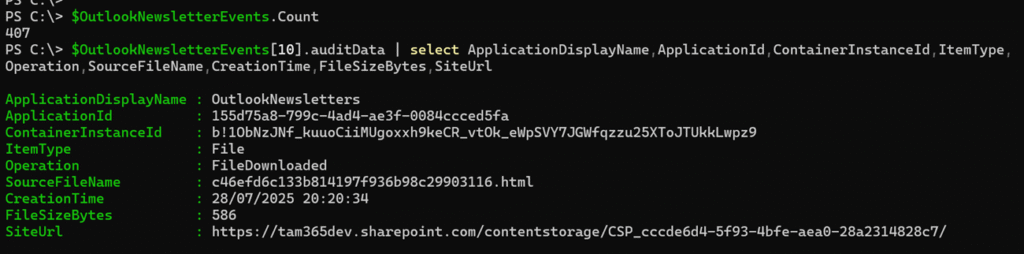
Next, list all unique operations to see which activities are included.
$OutlookNewsletterEvents.auditData | sort Operation | select Operation -Unique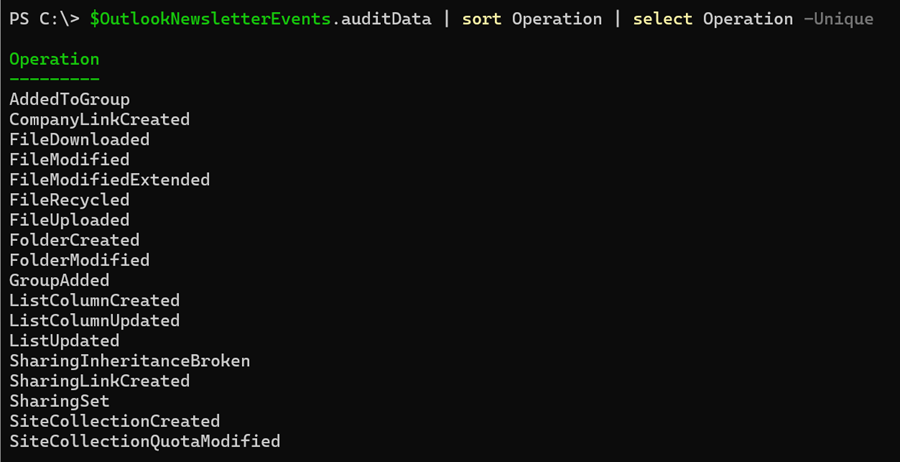
There are two interesting operations in the results:
- SiteCollectionQuotaModified
- FileRecycled
Let’s take SiteCollectionQuotaModified. After filtering for this operation, there’s only one matching activity.
($OutlookNewsletterEvents.auditData | ?{$_.Operation -eq "SiteCollectionQuotaModified"}).EventData
What the audit log reveals is questionable. The container was initially created with the tenant’s configured storage limit, but Microsoft silently increased it to the full 25 TB. SharePoint admins cannot modify the quota for these SharePoint Embedded containers.
Converted into a readable format:
| Tag | Description | Value (bytes) | Converted |
|---|---|---|---|
| <STORAGE_MAXIMUM_LEVEL> | New configured storage quota | 27,487,790,694,400 | 25 TB |
| <STORAGE_WARNING_LEVEL> | New warning threshold | 0 | Disabled |
| <USERCODE_MAXIMUM_LEVEL> | User code resource limit | 0 | Not in use |
| <USERCODE_WARNING_LEVEL> | User code warning threshold | 0 | Not in use |
| <STORAGE_PREVIOUS_MAXIMUM_LEVEL> | Previous quota limit | 53,687,091,200 | 50 GB |
| <STORAGE_PREVIOUS_WARNING_LEVEL> | Previous warning threshold | 45,634,027,520 | 42.5 GB |
| <STORAGE_USED> | Current storage usage | 40,411 | ~39.5 KB |
FileRecycled
Three FileRecycled operations are included.
$OutlookNewsletterEvents.auditData | ?{$_.Operation -eq "FileRecycled"} | select CreationTime,Operation,ItemType,SourceFileName,SiteUrl,ContainerInstanceId | sort CreationTime -Descending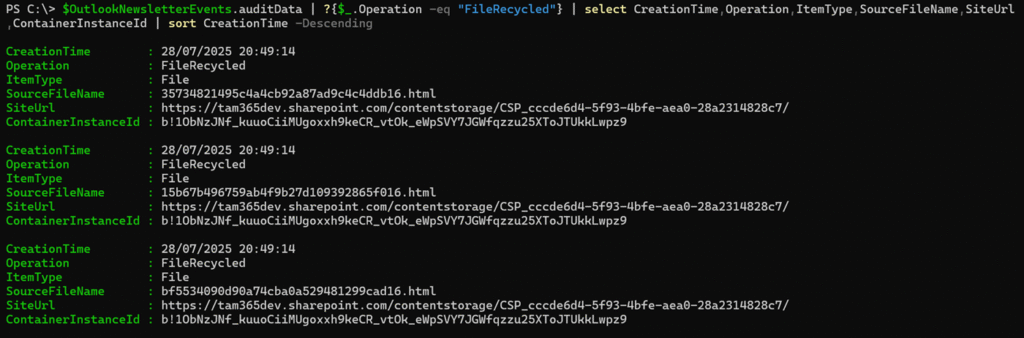
Not many deletions for a container that’s supposed to store draft content.
Folder structure
The audit logs also reveal the folder structure, giving you insight into how Microsoft organizes and stores the data within the container.
$OutlookNewsletterEvents.auditData.SourceRelativeUrl | sort | select -Unique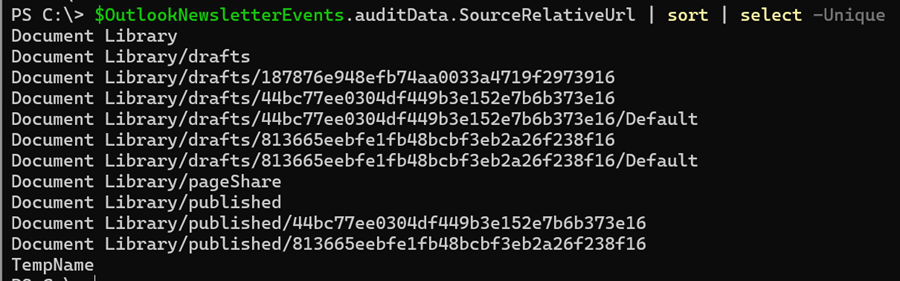
Each folder ID represents a newsletter edition. When an edition is published, the corresponding draft is not deleted.
Conclusion
Use your Purview Audit Logs to uncover what Microsoft is doing inside these unmanageable SharePoint Embedded containers. Monitor them closely, and proceed with caution. These containers are fully controlled by Microsoft, and there’s no communication or notification when changes occur within them.
