With virtualEventWebinar Microsoft Graph has a new API to list webinars. The API only includes read options for now. This option may help transfer webinar information to external systems.
The following permissions are worth noting for virtualEventWebinar:
- An app registration is required to list webinars. The listing of all webinars only supports application permission.
- With Delegated Permission, organizers could query their own webinars if the ID of the webinar is known (see example below).
- An application access policy in Teams is required for application permissions. The policy authorizes an app to list webinars for selected accounts.
The requirements and processes from Microsoft Graph can be summarized:
- App registration is connected to a new Application Access Policy in Teams.
- Application Access Policy is assigned to selected user accounts.
- The Application Access Policy authorizes Graph to list webinars for the user accounts. For Microsoft Graph it counts which account is the organizer.
Content
1) App registration for webinars
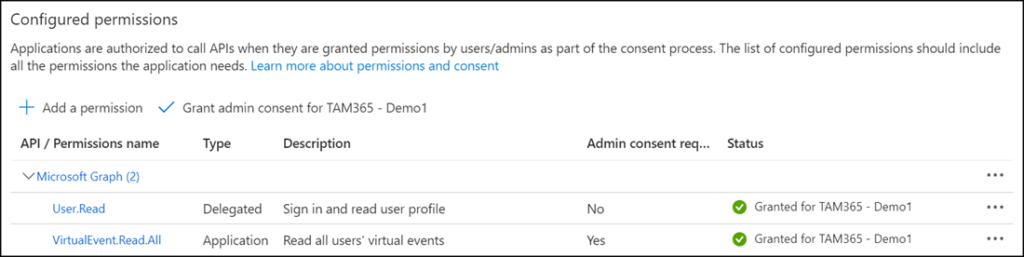
I created a new app registration with the VirtualEvent.Read.All permissions and uploaded my certificate for authentication in Entra ID. Only this permission is currently available for webinars.
2) Configure Application Access Policy in Teams
In the Graph documentation is a note about an Application Access Policy.
This API returns only webinars whose organizer has been assigned an application access policy.
The Application Access Policy instructions describe the process.
I created a new application access policy and connected the policy to the application ID of the app registration.
Import-Module MicrosoftTeams
Connect-MicrosoftTeams
$AppAccessPolicy = New-CsApplicationAccessPolicy -Identity "Webinar API Test" -AppIds "458636c5-d0b2-4efb-b9ac-371c18ad48ad"
I assigned the policy to an Entra ID group. Optionally, you can assign the policy to user accounts (User Assignment) or all employees (Global Assignment); see Grant-CsApplicationAccessPolicy.
Grant-CsApplicationAccessPolicy -PolicyName $AppAccessPolicy.Identity -Group "8667cfc4-6c88-4c11-8b98-e716d840de68"
Activation of the policy can take up to 30 minutes.
3) List webinars via Microsoft Graph
Once prepared, webinars should be available for authorized accounts via Graph.
Import-Module Microsoft.Graph.Authentication
Connect-MgGraph -ClientId "<AppID>" -CertificateThumbprint "<CertificateThumbprint>" -TenantId "<TenantID"
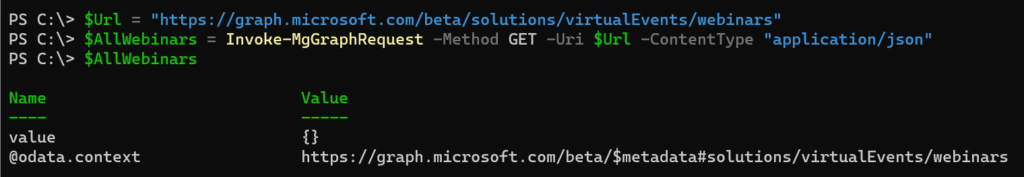
$Url = "https://graph.microsoft.com/beta/solutions/virtualEvents/webinars"
$AllWebinars = Invoke-MgGraphRequest -Method GET -Uri $Url -ContentType "application/json"
$AllWebinars.value
I found 16 webinars for my account. The list includes various test webinars from the past.
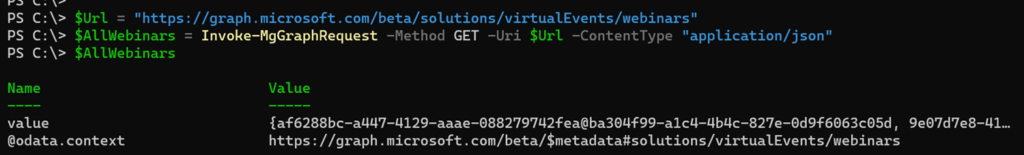
Graph includes information about name, status, audience, date, and other properties of each webinar. The available properties are described in the documentation.
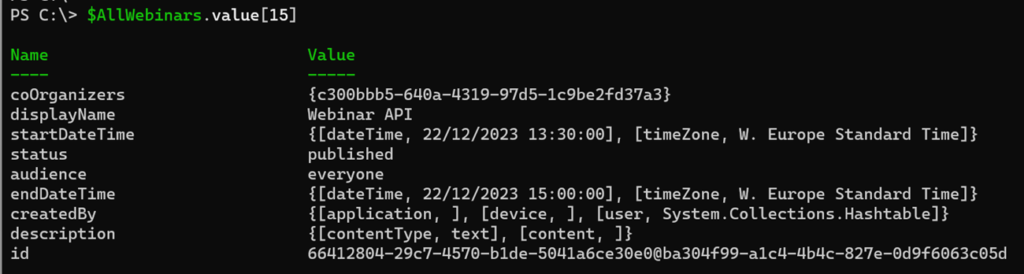
4) List webinar via ID
Microsoft describes listing a webinar using the Webinar ID in the documentation. The ID for a webinar is visible in Teams when the webinar is opened in Teams on the web and Manage Event is selected.
The address bar of your browser includes the ID 66412804-29c7-4570-b1de-5041a6ce30e0@ba304f99-a1c4-4b4c-827e-0d9f6063c05d. The ID can be used to query a single webinar.
Import-Module Microsoft.Graph.Authentication
Connect-MgGraph -ClientId "<AppID>" -CertificateThumbprint "<CertificateThumbprint>" -TenantId "<TenantID"
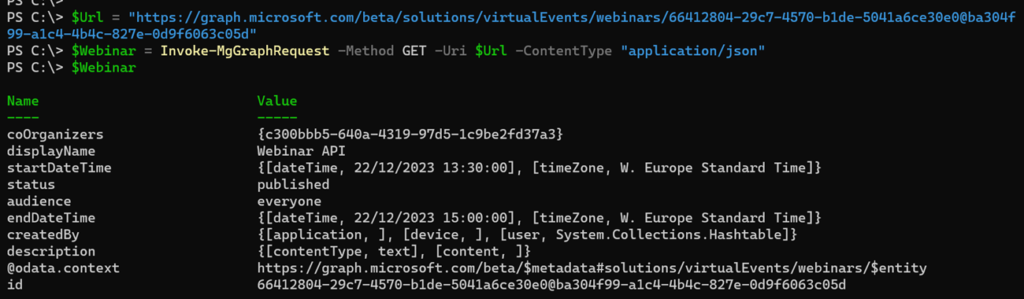
$Url = "https://graph.microsoft.com/beta/solutions/virtualEvents/webinars/66412804-29c7-4570-b1de-5041a6ce30e0@ba304f99-a1c4-4b4c-827e-0d9f6063c05d"
$Webinar = Invoke-MgGraphRequest -Method GET -Uri $Url -ContentType "application/json"
$Webinar
5) Remove Application Access Policy from user account
The assignment of the Application Access Policy can be removed again. In my example, I remove the assignment from the group.
Grant-CsApplicationAccessPolicy -Group "8667cfc4-6c88-4c11-8b98-e716d840de68" -PolicyName $null
As a result, the query from Step 3 no longer includes webinars.