1Password has informed their extensions for browsers (beta release) now support login with Passkey. When logging in with Passkey the classic password is no longer needed. If you don’t know Passkey yet you can read more details about the future of passwordless login at FIDO Alliance.
What are Passkeys?
Passkeys are a password replacement that provide faster, easier, and more secure sign-ins to websites and apps across a user’s devices. Unlike passwords, passkeys are resistant to phishing, are always strong, and are designed so that there are no shared secrets.
From a technical standpoint, passkeys are “discoverable” FIDO credentials for passwordless authentication. The cryptographic keys are used from end-user devices (computers, phones, or security keys) that are used for secure user authentication.
1Password maintains a public directory of websites that already support Passkey login. Microsoft is also listed. For the configuration in a Microsoft account the directory refers to the help.

Since I use 1Password myself I tried Passkey with my Microsoft accounts (personal and organization accounts). My colleague Andres Bohren tried Passkey with a Google account.
Generally for information, to set up the 1Password browser extensions you need a 1Password account. You have to log in to the browser extension with your 1Password account. Logging in with Passkey currently only works through the browser extension. Passkey is synchronized in the 1Password apps, but the apps and operating systems are not ready to support the login possibility.
Content
Setup for Microsoft personal account
- Install the 1Password extension (beta release) for your browser and log in with your 1Password account. If you have already installed 1Password locally on your client the setup in the browser takes less than 30 seconds.
- Open the account settings for your Microsoft account > Security > Advanced Security.
- Add a new security method and select Security Key.
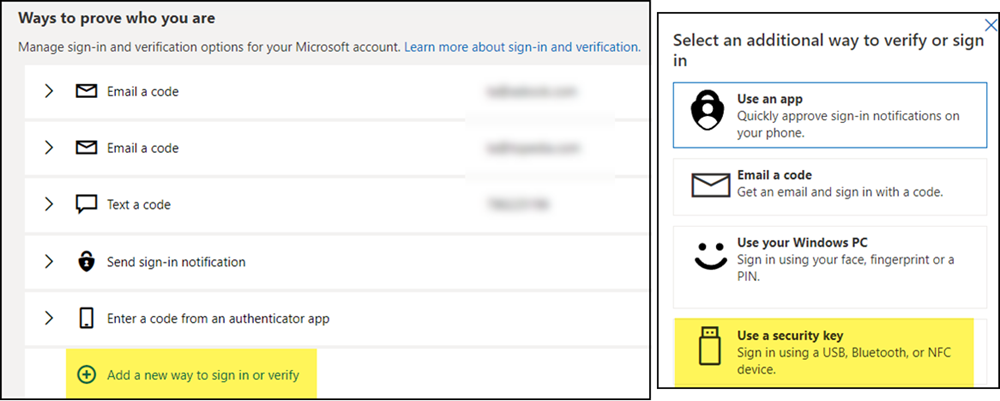
- Select USB device as key. For a login with Passkey in a personal Microsoft account you don’t need the classic hardware key. The 1Password browser extension takes over.
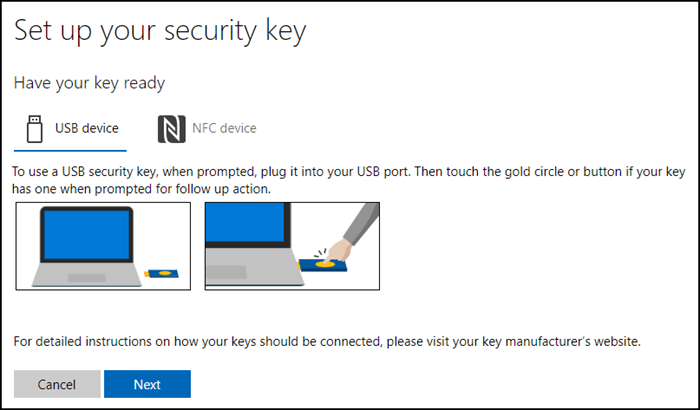
- Microsoft will ask how to create the Passkey. If the 1Password browser extension is installed 1Password will suppress the dialog and ask which account to link the Passkey instead.
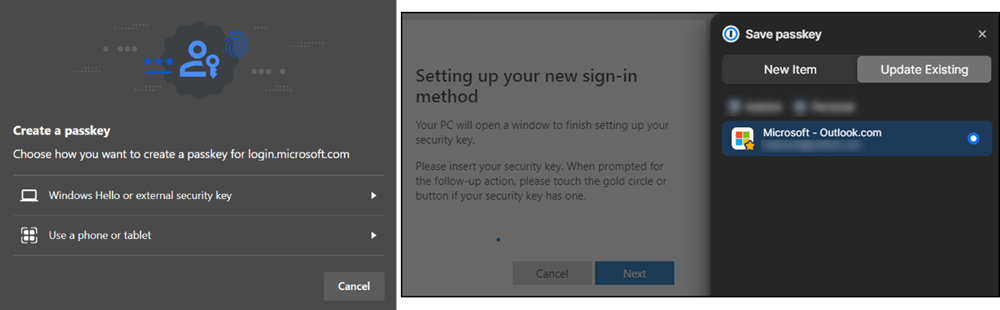
- Now you have to name the Passkey, the setup is then confirmed.
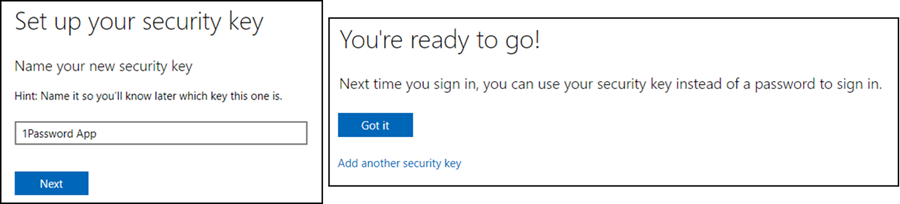
1Password has saved the Passkey. In the 1Password item you could delete the Passkey from 1Password or revoke the Passkey in your Microsoft account and set it up again.

Login with Passkey in (personal) Microsoft account
Log out of your account or open a new, private browser session.
- Open (for example) Outlook Mail.
- Select the login method Windows Hello / Security Key.
- The 1Password browser extension informs about the login with Passkey.
- That’s it, the login is done.
Setup for organization accounts
Since Azure AD supports the configuration options from a personal account too, I tried to configure the Passkey setup in Azure AD.
Until the last step (the final setup of Passkey) the configuration and initial setup works. At the last step Microsoft shows an error and the setup cannot be completed. Eventually Azure AD does not support a login type like that of 1Password so far.
Configuration in Azure AD
In Azure AD login with FIDO2 Security Keys should be possible. I enabled the authentication method for FIDO2 keys in Azure AD.
- Open Azure AD > Security > Authentication methods > Authentication methods and select the method for FIDO2 Security Keys.
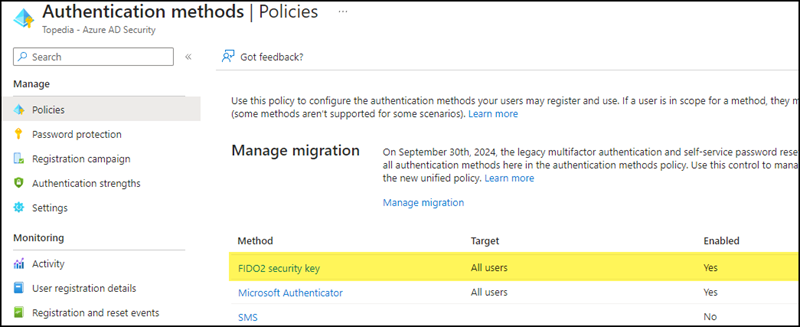
- Enable the method for all user accounts or a selected Azure AD group.
- Also check the advanced configurations. In my case I use the default configuration. Disabling enforce attestation does not help with 1Password Passkey. Cloudbrothers describes the individual configurations in a good form.
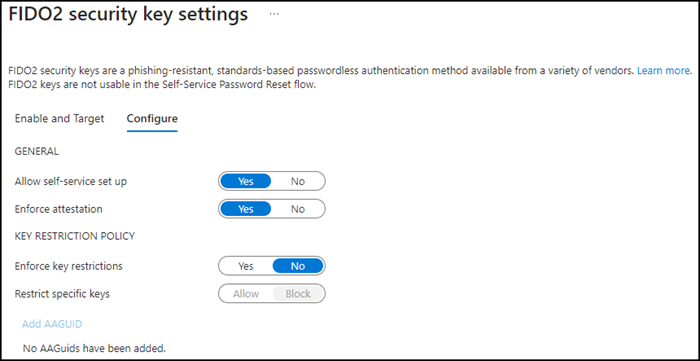
- Save the configuration.
Activation for your organization account
Install the 1Password extension (beta release) for your browser and log in with your 1Password account. If you have already installed 1Password locally on your client the setup in the browser takes less than 30 seconds.
After activation open My account > Security Info with your Azure AD account, add a new security method and select Security Key. The system will ask you to confirm the setup via multi-factor authentication.
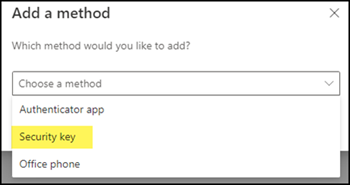
Select USB device as key and confirm the next dialog.
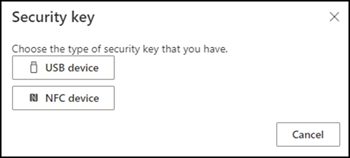
Microsoft will ask how to create the Passkey. If the 1Password browser extension is installed 1Password will suppress the dialog and ask which account to link the Passkey instead. 1Password saves/updates the Passkey in your item.
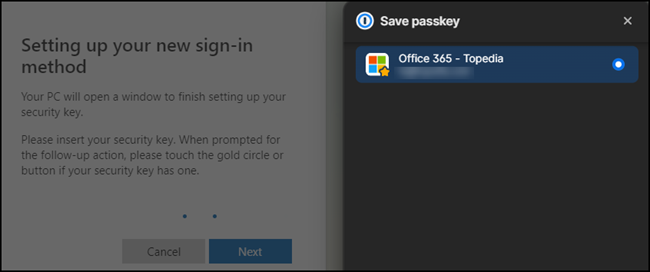
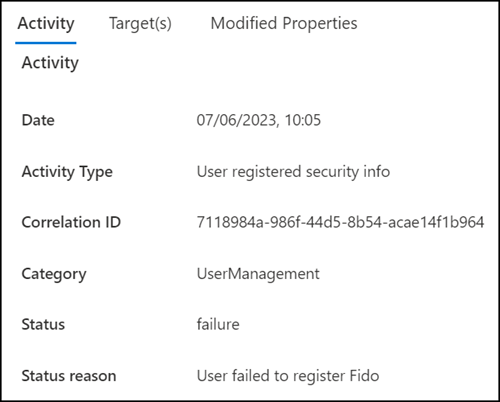
Finally, Microsoft wants to know how the Passkey should be named and shows the mentioned error when completing the configuration.
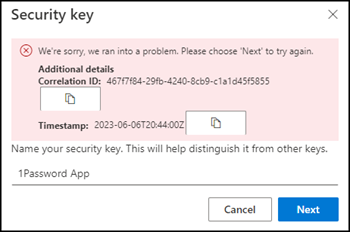
Azure AD notes the setup error with a failed audit item.
My conclusion for organization accounts
Compared to personal accounts it seems for me Azure AD still requires a classic hardware key for login. For now, Azure AD cannot handle the login type if you use the 1Password browser extension.
