Microsoft is rolling out four new Entra ID admin roles for SharePoint and Copilot Agent Administrators.
- SharePoint Advanced Management Administrator
- Agent ID Administrator
- Agent ID Developer
- Agent Registry Administrator
Note:
These roles are new and may take some time to become fully active, as Microsoft has not yet officially communicated their availability.
Content
SharePoint Advanced Management Administrator
The SharePoint Advanced Management Administrator role is designed for users who require elevated administrative capabilities beyond the standard SharePoint Administrator role. It allows full global management of SharePoint Online, including service configuration, support ticket management, and monitoring service health.
In addition, this role provides enhanced visibility into SharePoint content by allowing administrators to view file, folder, library, document, and list names, paths, and URLs, without granting access to the actual file or item content.
The role also enables administrators to remove permissions from files, folders, libraries, documents, and lists across SharePoint sites, giving them greater control over access remediation and security management.
A comparison of both admin roles shows that the new role includes all permissions of the SharePoint Administrator role, plus full access to the SharePoint Advanced Management (SAM) features. It’s important not to misinterpret this as a SAM-only role. This role has access to SAM features and full SharePoint administrative privileges.
The template ID is 99009c4a-3b3f-4957-82a9-9d35e12db77e.
| SharePoint Administrator role permissions | SharePoint Advanced Management Administrator role permissions |
|---|---|
| microsoft.azure.serviceHealth/allEntities/allTasks | microsoft.azure.serviceHealth/allEntities/allTasks |
| microsoft.azure.supportTickets/allEntities/allTasks | microsoft.azure.supportTickets/allEntities/allTasks |
| microsoft.backup/oneDriveForBusinessProtectionPolicies/allProperties/allTasks | microsoft.backup/oneDriveForBusinessProtectionPolicies/allProperties/allTasks |
| microsoft.backup/oneDriveForBusinessRestoreSessions/allProperties/allTasks | microsoft.backup/oneDriveForBusinessRestoreSessions/allProperties/allTasks |
| microsoft.backup/restorePoints/sites/allProperties/allTasks | microsoft.backup/restorePoints/sites/allProperties/allTasks |
| microsoft.backup/restorePoints/userDrives/allProperties/allTasks | microsoft.backup/restorePoints/userDrives/allProperties/allTasks |
| microsoft.backup/sharePointProtectionPolicies/allProperties/allTasks | microsoft.backup/sharePointProtectionPolicies/allProperties/allTasks |
| microsoft.backup/sharePointRestoreSessions/allProperties/allTasks | microsoft.backup/sharePointRestoreSessions/allProperties/allTasks |
| microsoft.backup/siteProtectionUnits/allProperties/allTasks | microsoft.backup/siteProtectionUnits/allProperties/allTasks |
| microsoft.backup/siteRestoreArtifacts/allProperties/allTasks | microsoft.backup/siteRestoreArtifacts/allProperties/allTasks |
| microsoft.backup/userDriveProtectionUnits/allProperties/allTasks | microsoft.backup/userDriveProtectionUnits/allProperties/allTasks |
| microsoft.backup/userDriveRestoreArtifacts/allProperties/allTasks | microsoft.backup/userDriveRestoreArtifacts/allProperties/allTasks |
| microsoft.directory/groups/hiddenMembers/read | microsoft.directory/groups/hiddenMembers/read |
| microsoft.directory/groups.unified/assignedLabels/update | microsoft.directory/groups.unified/assignedLabels/update |
| microsoft.directory/groups.unified/basic/update | microsoft.directory/groups.unified/basic/update |
| microsoft.directory/groups.unified/create | microsoft.directory/groups.unified/create |
| microsoft.directory/groups.unified/delete | microsoft.directory/groups.unified/delete |
| microsoft.directory/groups.unified/members/update | microsoft.directory/groups.unified/members/update |
| microsoft.directory/groups.unified/owners/update | microsoft.directory/groups.unified/owners/update |
| microsoft.directory/groups.unified/restore | microsoft.directory/groups.unified/restore |
| microsoft.office365.migrations/allEntities/allProperties/allTasks | microsoft.office365.migrations/allEntities/allProperties/allTasks |
| microsoft.office365.network/performance/allProperties/read | microsoft.office365.network/performance/allProperties/read |
| microsoft.office365.serviceHealth/allEntities/allTasks | microsoft.office365.serviceHealth/allEntities/allTasks |
| microsoft.office365.sharePointAdvancedManagement/allEntities/allProperties/allTasks | |
| microsoft.office365.sharePoint/allEntities/allTasks | microsoft.office365.sharePoint/allEntities/allTasks |
| microsoft.office365.supportTickets/allEntities/allTasks | microsoft.office365.supportTickets/allEntities/allTasks |
| microsoft.office365.usageReports/allEntities/allProperties/read | microsoft.office365.usageReports/allEntities/allProperties/read |
| microsoft.office365.webPortal/allEntities/standard/read | microsoft.office365.webPortal/allEntities/standard/read |
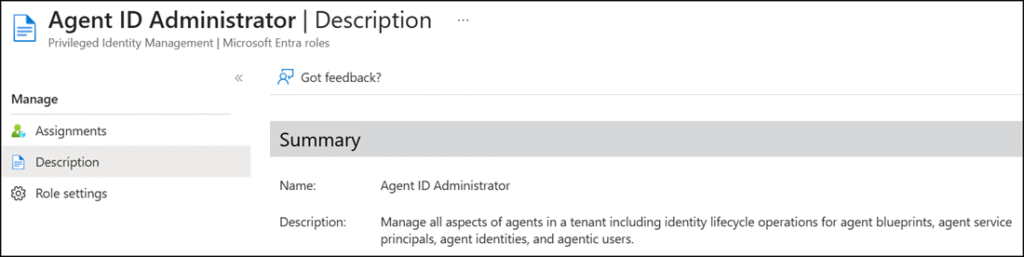
Agent ID Administrator
Based on the role description, the Agent ID Administrator role manages all aspects of agents within a tenant, including the full identity lifecycle for agent blueprints, agent service principals, agent identities, and agentic users.
However, based on the permissions, this role is designed for users who manage Access Reviews, group lifecycle, and governance in Microsoft Entra ID. It allows creating, updating, and deleting Access Reviews for groups, applications, and entitlement management. The role can also read hidden group membership, create Microsoft 365 groups (as owner), and view organizational and policy information.
Additionally, the role includes permissions to read and configure Service Health, and to create and manage Microsoft 365 and Azure support tickets, giving the user a support-oriented, governance-focused scope.
Template ID: db506228-d27e-4b7d-95e5-295956d6615f
Role permissions:
microsoft.azure.serviceHealth/allEntities/allTasks
microsoft.azure.supportTickets/allEntities/allTasks
microsoft.directory/accessReviews/definitions.applications/allProperties/allTasks
microsoft.directory/accessReviews/definitions.directoryRoles/allProperties/read
microsoft.directory/accessReviews/definitions.entitlementManagement/allProperties/allTasks
microsoft.directory/accessReviews/definitions.groups/allProperties/read
microsoft.directory/accessReviews/definitions.groups/allProperties/update
microsoft.directory/accessReviews/definitions.groups/create
microsoft.directory/accessReviews/definitions.groups/delete
microsoft.directory/externalUserProfiles/standard/read
microsoft.directory/groups/hiddenMembers/read
microsoft.directory/groups.unified/createAsOwner
microsoft.directory/organization/standard/read
microsoft.directory/policies/standard/read
microsoft.office365.serviceHealth/allEntities/allTasks
microsoft.office365.supportTickets/allEntities/allTasks
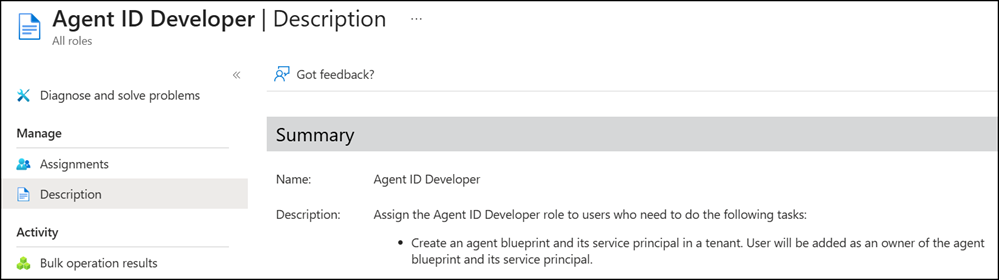
Agent ID Developer
The Agent ID Developer role allows users to create agent blueprints and their associated service principals within a tenant. When a user creates one, they automatically become the owner of both the agent blueprint and its service principal.
Microsoft mentioned these agent blueprints in September, related to Agent Factory.
Trust is rapidly becoming the defining challenge for enterprise AI. If observability is about seeing, then security is about steering. As agents move from clever prototypes to core business systems, enterprises are asking a harder question: how do we keep agents safe, secure, and under control as they scale?
The answer is not a patchwork of point fixes. It is a blueprint. A layered approach that puts trust first by combining identity, guardrails, evaluations, adversarial testing, data protection, monitoring, and governance.
Template ID: db506228-d27e-4b7d-95e5-295956d6615f
Role permissions: microsoft.directory/servicePrincipals/standard/read
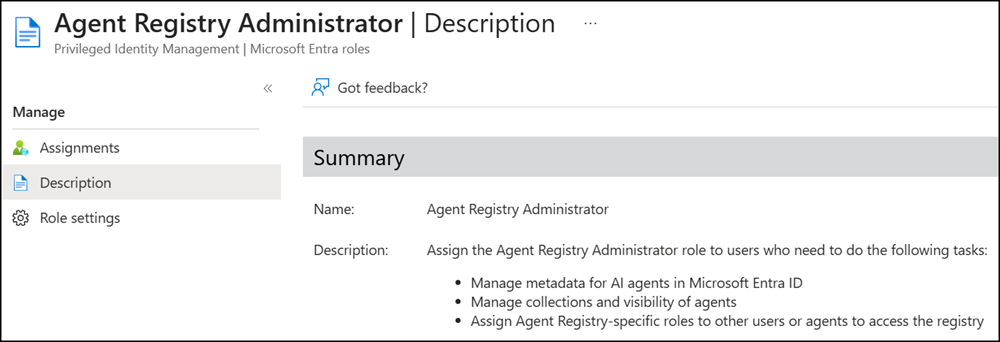
Agent Registry Administrator
The Agent Registry Administrator role manages metadata and visibility for AI agents in Microsoft Entra ID. Users with this role can organize agents into collections and control who can access the agent registry. They can also assign Agent Registry-specific roles to other users or agents.
Microsoft mentioned the agent registry in August as part of its efforts to secure and govern autonomous agents, including references on its developer blog.
An emerging strategy to manage AI agents at scale and improve risk management is the concept of an agent registry. While the directory of Microsoft Entra ID is an authoritative source for both human users and application artifacts, there is a need to provide a similar authoritative store for all agent-specific metadata. This is where the concept of an agent registry comes in—serving as a natural extension to the directory, tailored to capture the unique attributes, relationships, and operational context of AI agents as they proliferate across the enterprise. As these registries evolve, they are likely to integrate with core components like MCP servers, reflecting the expanding role of agents within the ecosystem.
Template ID: 6b942400-691f-4bf0-9d12-d8a254a2baf5
Role permissions: microsoft.agentRegistry/allEntities/allProperties/allTasks
