Until now, it was not possible to save a passkey from an Entra ID organization account in a password manager like 1Password. The Entra ID passkey was limited as a device-bound passkey, meaning you could store it on your Windows device, the Microsoft Authenticator app, or other supported devices. If you tried to store such a passkey in 1Password, you would receive an error.
A password manager like 1Password requires multi-device passkeys.
Multi device passkeys
Multi device passkeys (MDC) are credentials that can be moved and synced between devices. This means that if a user has multiple devices, they can use the built in authenticator to validate a credential regardless if they are using the device that was used to create the credential.
This offers a higher degree of usability as users will be able to utilize any of their devices to authenticate into services without having to individually enroll each one. MDC’s may also be shared between different users; for example you can AirDrop your passkey to another person in the case of shared accounts.
MDC’s are commonly embedded into other devices like a mobile phone, or laptop. Platforms that will support MDC are Windows Hello, Apple Face/Touch ID, and Android Biometrics.
Entra ID now supports synced passkeys in Public Preview (rolling out, should be available by December 2025). A synced passkey is a multi-device passkey that you can store in a password manager like 1Password. 🎉
Passkeys (FIDO2) are a strong, phishing resistant alternative to passwords. With this preview, Microsoft Entra ID supports synced passkeys. Synced passkeys are stored in platform or with other passkey providers such as Apple iCloud Keychain, Google Password Manager, 1Password, or Bitwarden, and made available across a user’s devices. Synced passkeys simplify user onboarding and account recovery, which accelerates passwordless adoption for most organizations.
- You must configure a new passkey profile in Entra ID, as synced passkeys are part of it.
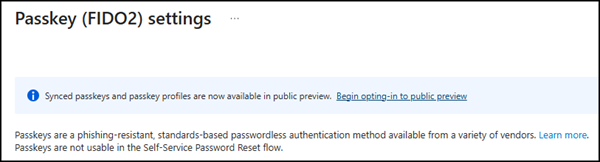
Open Entra ID > Authentication Methods, select Passkey (FIDO2), then opt-in to the Public Preview for synced passkeys.
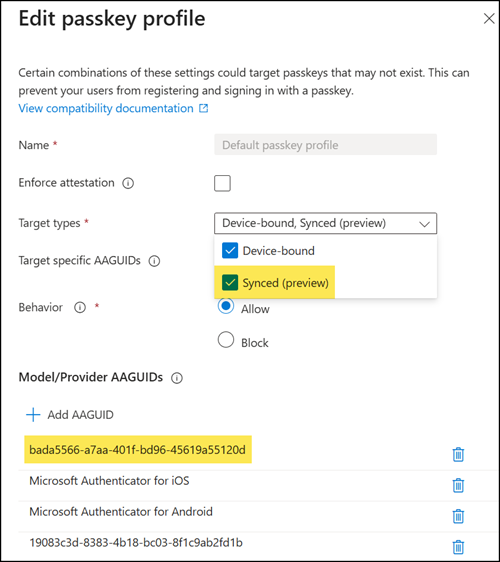
- Entra ID requires a default passkey profile, which you need to configure first. You can create up to three profiles during the preview. A passkey profile defines which passkey policy applies to which group of users; for example, you may allow synced passkeys for standard users but not for privileged accounts, and specific accounts require a defined FIDO2 key.
- Enable the target type “Synced (preview)” for the passkey profile. Enforce attestation is not supported for synced passkeys.
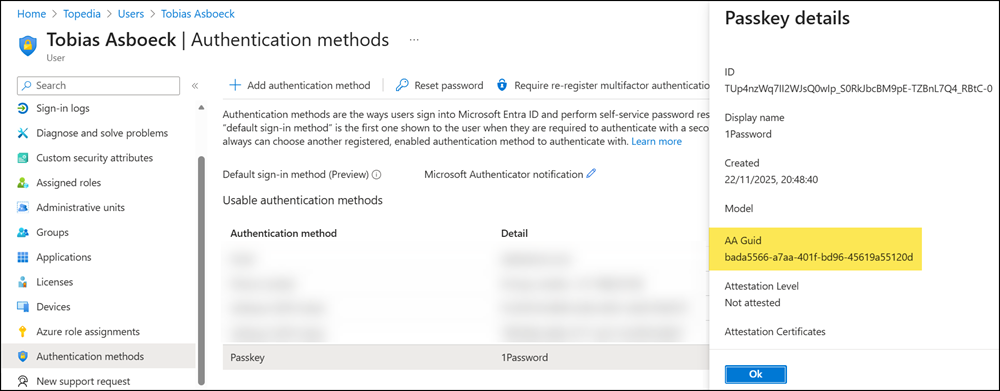
- The provider GUID for 1Password is bada5566-a7aa-401f-bd96-45619a55120d, as posted in the 1Password community two years ago when passkeys were first introduced in Entra ID.
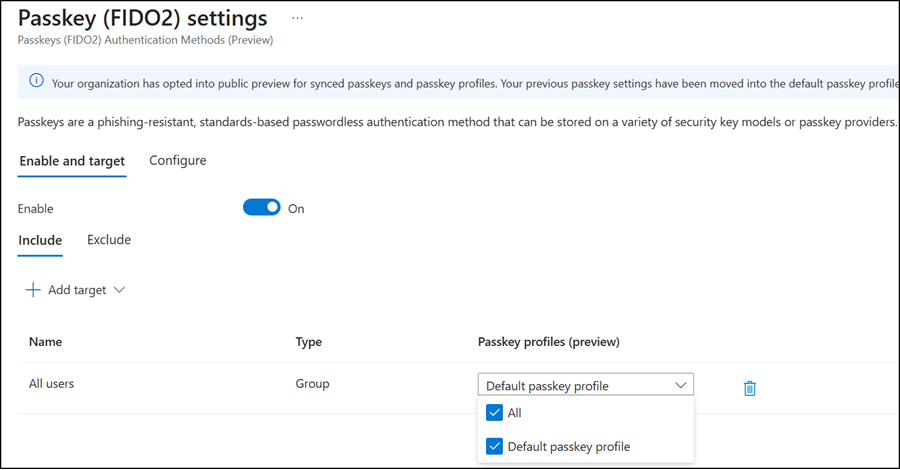
- Assign the passkey profile to your passkey authentication method.
- You’re now ready to configure a new passkey for your account.
Open mysignins.microsoft.com/security-info and add a new sign-in method. You will now see the updated Passkey method. Previously, this was Security Key.
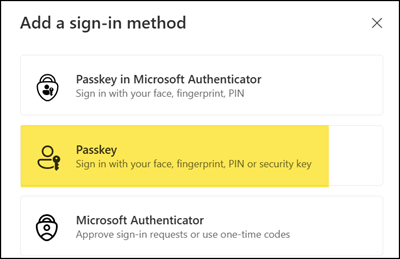
- Follow the steps to configure and store your passkey in 1Password. Both the Microsoft system and 1Password will guide you through the process. It takes less than a minute.
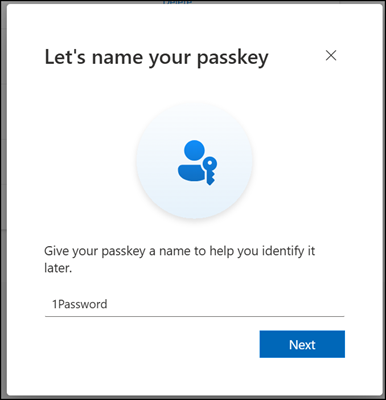
- Your synced passkey has been created and is now listed in your sign-in methods.
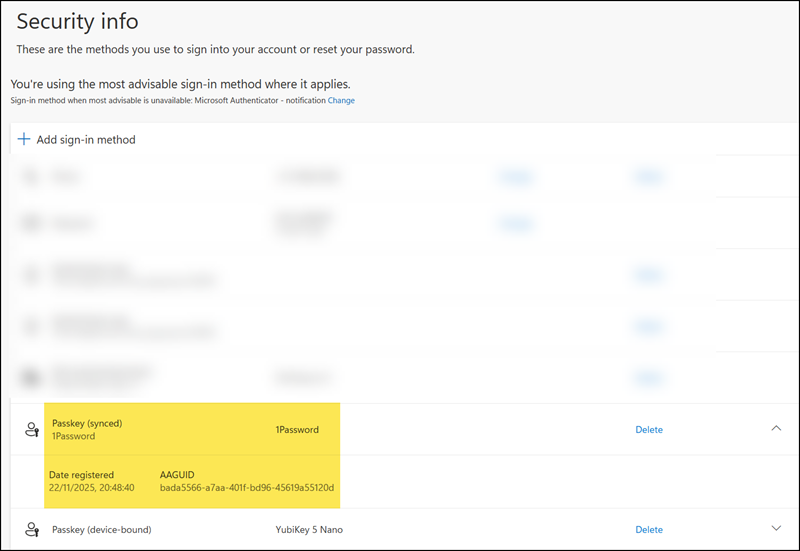
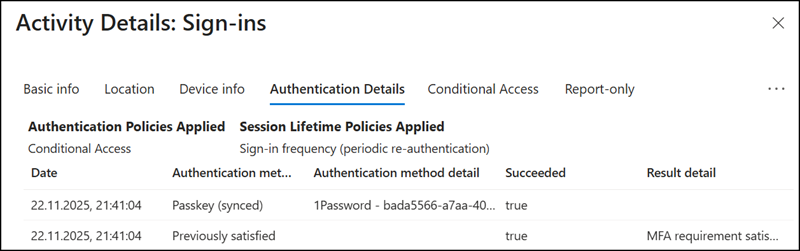
The provider GUID is also confirmed in the authentication methods of my Entra ID account.
To test it, open a private browser session and sign-in at m365.cloud.microsoft.
Select the passkey sign-in option and then choose the 1Password login offered by 1Password. You’re in, without entering your username, password, or MFA code. This is truly seamless authentication.
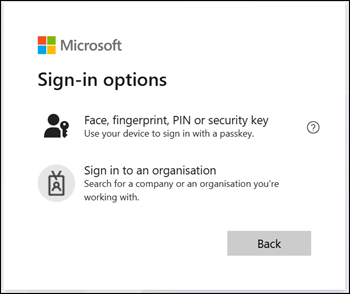
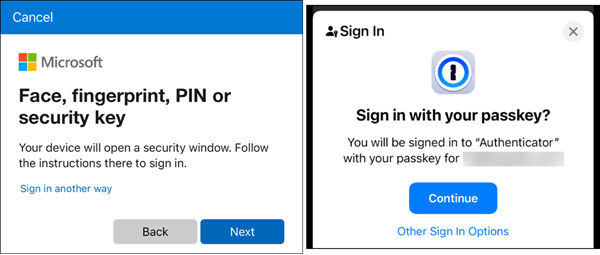
A synced passkey works seamlessly across your other devices, such as your mobile phone.
The Entra ID sign-in log lists the passkey-based sign-in.