At Build 2025, Microsoft introduced Microsoft Entra Agent ID to find AI Agents in Entra ID.
Just open Enterprise Applications in Entra ID and filter for the application type Agent ID.
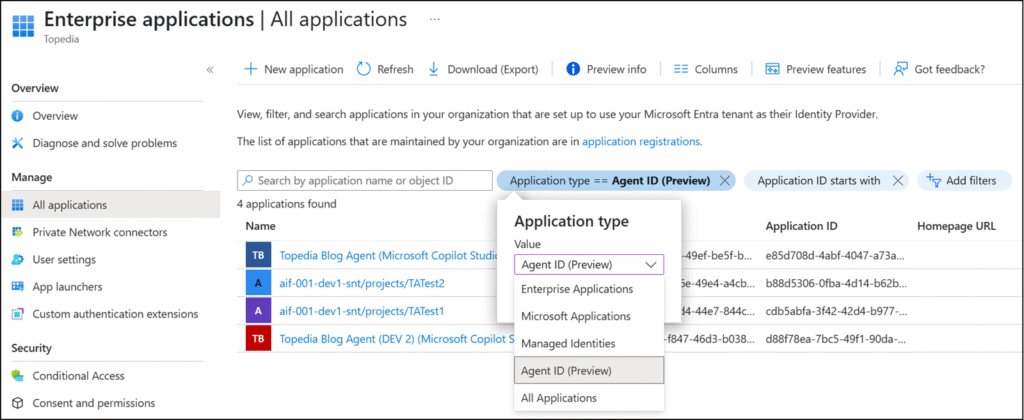
If you analyze what Entra ID is doing for the filter, it’s a simple query for service principal tags with the following values:
- tags startswith power-virtual-agents- OR
- tags is equal AgenticInstance OR
- tags is equal AgenticApp
- filter the first 100
You can do the same, as Entra ID is querying the servicePrincipals resource in the background.
I recommend checking your Agent ID service principals. I think you will find some interesting changes.
# Filter Agent ID service principals with Microsoft Graph.
# Note that you getting the first 100 service principals with the filter.
Import-Module Microsoft.Graph.Authentication
Connect-MgGraph -Scopes "Application.Read.All"
$Header = @{ "ConsistencyLevel" = "eventual" }
$Url = "https://graph.microsoft.com/v1.0/servicePrincipals?`$count=true&`$filter=(tags/Any(p: startswith(p, 'power-virtual-agents-')) or tags/Any(p: p eq 'AgenticInstance') or tags/Any(p: p eq 'AgenticApp'))&`$top=100"
$Result = Invoke-MgGraphRequest -Method Get -Uri $Url -Headers $Header
$Result.value
Content
Copilot Studio Service Principals
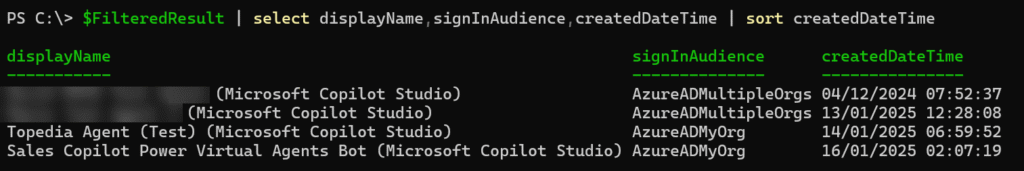
- Microsoft changed the signInAudience in January. Until then, the signInAudience for all newly created Copilot Studio Agents was an AzureADMultipleOrgs service principal. Microsoft changed this to AzureADMyOrg in January for new Copilot Studio service principals.
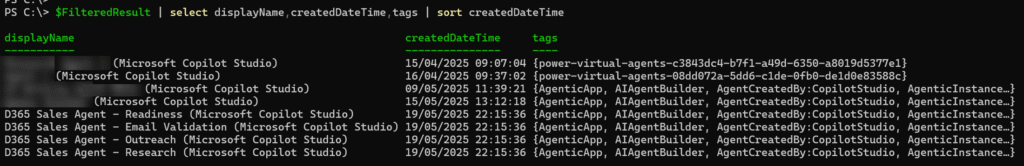
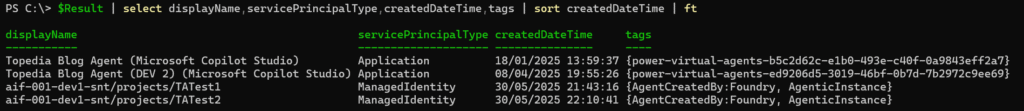
- Since May, Microsoft has been adding the Agent ID tags to all new Copilot Studio service principals.
Previously, there was just the tag “power-virtual-agents-[AgentID].” Now, there are the additional tags: AgenticInstance, AgenticApp, AIAgentBuilder, and AgentCreatedBy:CopilotStudio
- All Copilot Studio service principals include the Power Platform environment where they are hosted in the description.
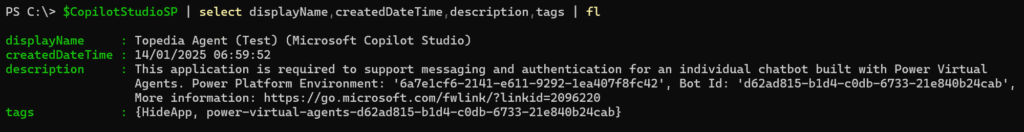
You can extract the environment ID. The tag power-virtual-agents- includes the agent ID from the environment.
# Extract the Power Platform environment from the service principal description
if ($CopilotStudioSP.description -match "Power Platform Environment: '([0-9a-fA-F\-]{36})'") {
$envGuid = $matches[1]
Write-Output "Extracted GUID: $envGuid"
}
Azure AI Foundry Service Principals
An Azure AI Foundry service principal is a Managed Identity compared to Copilot Studio service principals and includes the tags AgentCreatedBy:Foundry and AgenticInstance. A new Azure AI Foundry project creates a new Managed Identity.
The Microsoft presentation mentioned that the agent should be visible in the Enterprise apps. In my case, the Azure AI Foundry project creates a Managed Identity, not the agent in the project.
Edit:
The Microsoft demo about the Azure AI Foundry agent was not adequately prepared. Microsoft named the agent with the same title as the project. As a result, the customer sees the project name in the demo, not the modified agent.
The documentation mentions the scoping:
Agents are scoped at the project level, which ensures data isolation—agents within the same project share access to the same resources.

This is great info. Can you share how one goes about reverse engineering the filter that EntraID is using for Enterprise applications filter “Agent ID (Preview)”?
Hi Jeff, do you mean removing the filter? Just click the X next to it, or simply refresh the page to clear all filters.
What I mean is that you mentioned that you investigated what the Enterprise App filter “Agent ID (Preview)” was doing and found that it was filtering based on tags startswith power-virtual-agents- OR tags is equal AgenticInstance OR tags is equal AgenticApp tags is equal AgenticApp
I was interested to know how you went about figuring out that the Enterprise App filter “Agent ID (Preview)” was leveraging those specific tags. I attempted doing f12 debug mode in IE and then applying the filter “Agent ID (Preview)” but nothing jumped out at me. This is more for my own knowledge for being able to reverse engineer any new filters like this in the future.
Ah, thanks for the clarification. You’re right, I used the browser’s developer tools to capture the API call.
If you switch the filter to “Agent ID (Preview)”, you’ll notice a batch request to the servicePrincipals endpoint with the following filter:
“$filter=(tags/Any(p: startswith(p, ‘power-virtual-agents-‘)) or tags/Any(p: p eq ‘AgenticInstance’) or tags/Any(p: p eq ‘AgenticApp’))”
I reused the same filter for my own Graph API call.
I just tested it again, same result. To verify, filter for $batch in the network log and inspect the request payload for a servicePrincipals call. There is more than one batch call. One of these calls includes the filter.