Microsoft extended the Microsoft 365 Copilot license with a limited version of Viva Pulse last December.
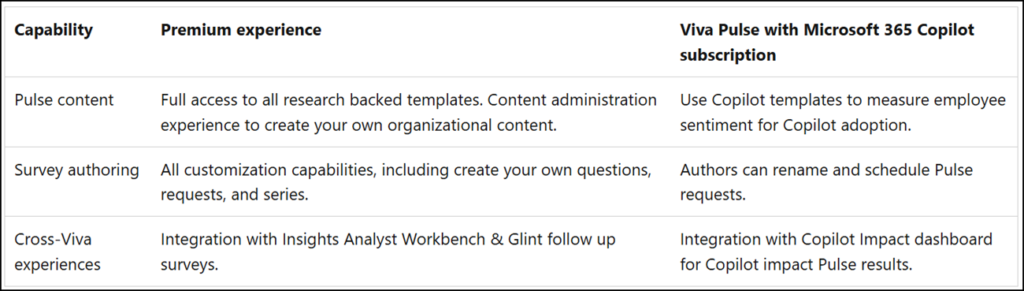
Below is a license comparison for Viva Pulse Premium (included in Viva Workplace Analytics and Employee Feedback and Viva Suite license) vs. Viva Pulse with Microsoft 365 Copilot.
Last December, I asked Microsoft how to control Viva Pulse for users with a Microsoft 365 Copilot license.
Viva Pulse had no such control or feature policy. By default, Viva Pulse is always enabled for such users at pulse.viva.cloud.microsoft or via the Viva Pulse app in Teams (if not restricted). That means everyone in your organization with a Microsoft 365 Copilot license can prepare and send Pulse requests to all internal users.
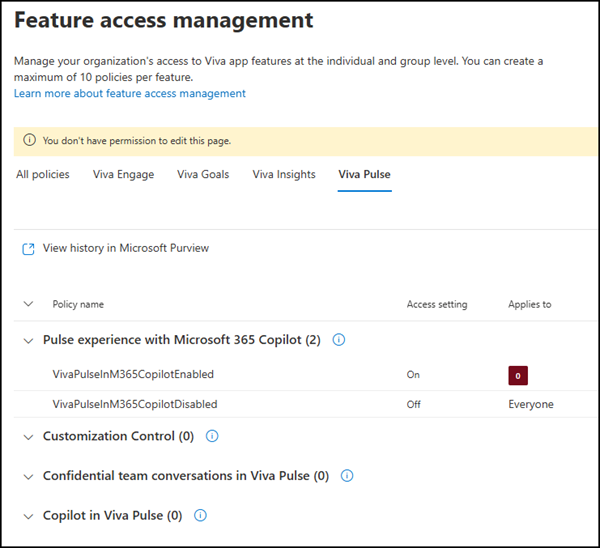
Now, the Viva Pulse feature access policies were extended with two new policies:
- Pulse experience with Microsoft 365 Copilot
- Copilot in Viva Pulse
Pulse experience with Microsoft 365 Copilot is the new policy that controls whether users can create and send Viva Pulse requests to internal users. This policy is perfect for limiting who can prepare and send such requests but does not impact who can respond to Pulse requests.
Pulse experience with Microsoft 365 Copilot
Users with a Microsoft 365 Copilot license can create and send Pulse requests to users in the tenant to gather real-time feedback about Copilot implementation from their teams. … This capability is default turned on for your tenant.
Viva Pulse licensing
A licensing reminder for Viva Pulse:
- Users need a Microsoft 365 Copilot license to prepare a Copilot Pulse request. Microsoft prepared three templates for Microsoft 365 Copilot, that’s it. Users have no options to prepare other requests.
- Users need a Viva Pulse Premium license for the full feature pack, which includes the ability to prepare custom requests.
- Internal users need a license/service plan for Microsoft Forms. They don’t need a Viva Pulse license to respond to such requests.
How to configure Viva Pulse feature policies
I recommend configuring the Viva Pulse policies with PowerShell, but you can also do this in the Microsoft 365 admin center. However, from my experience, the feature access management configuration has ongoing issues and errors if you do this configuration in the admin center. Sometimes, it’s working, but most of the time, there is an issue.
It’s a frustration with the admin center, do it with PowerShell. It’s pretty simple.
- For both cases, you need either the Viva Pulse admin role (recommended) or Global Administrator.
- You need the Exchange Online PowerShell module, which includes all Viva commands. You don’t need the Exchange admin role.
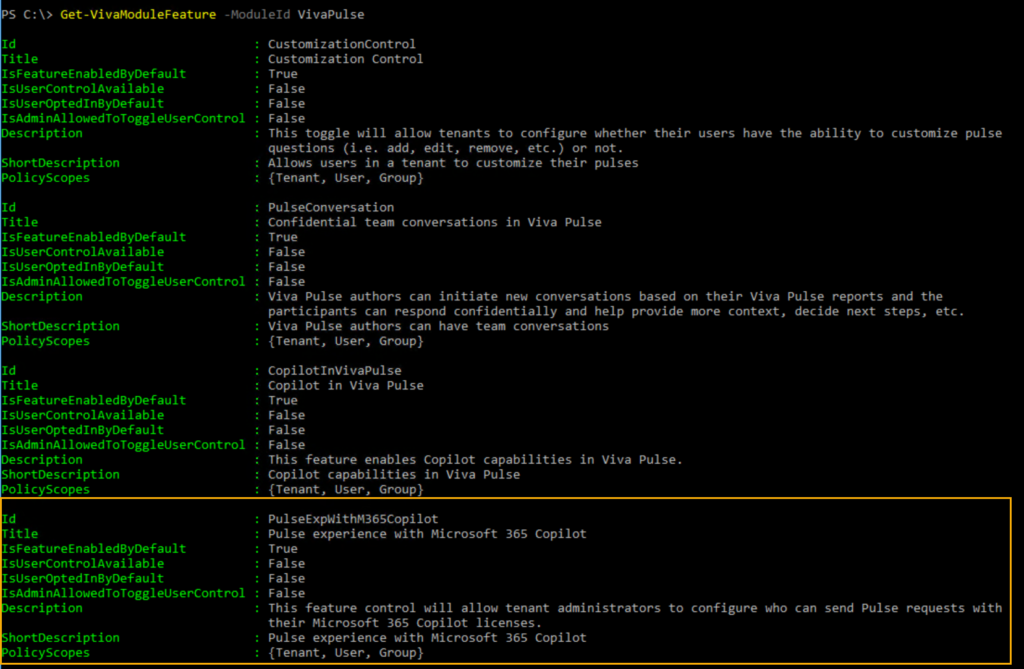
First, connect to Exchange Online and get all the feature policies for the Viva Pulse module. The documentation lists all the Viva modules and internal feature names.
With PowerShell, you can find some interesting information (which is not available if you do the configuration in the admin center), such as whether the feature is enabled by default or if users can opt out (depending on the Viva module and feature).
Connect-ExchangeOnline
Get-VivaModuleFeature -ModuleId VivaPulse
In my example, my required feature Pulse experience with Microsoft 365 Copilot is enabled by default.
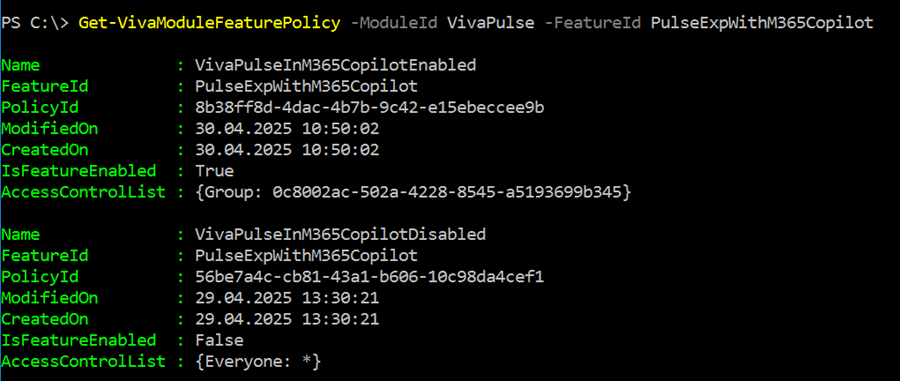
Second, check if you have configured a feature access policy already.
Get-VivaModuleFeaturePolicy -ModuleId VivaPulse -FeatureId PulseExpWithM365Copilot
Third, in my method, I whitelist those accounts that can send Pulse requests; all others are disabled.
Create a new feature access policy for Viva Pulse and disable the feature for all users. This is a tenant policy for Microsoft. Be careful with the policy name, many characters are blocked (spaces are allowed).
You can assign a maximum of 10 policies per feature to users and groups. Each policy can be assigned to a maximum of 20 users or groups. You can assign one additional policy per feature to the entire tenant by using the -Everyone parameter, which will function as a global default state for that feature across your organization.
Add-VivaModuleFeaturePolicy -ModuleId VivaPulse -FeatureId PulseExpWithM365Copilot -Name "VivaPulseInM365CopilotDisabled" -IsFeatureEnabled $false -Everyone
Fourth, enable the Viva Pulse feature for defined Copilot licensed users. You can use user accounts, Microsoft 365 groups, security groups created in or synchronized to Entra ID, or distribution groups.
You should read the details about policy precedence to know the impact if users are members of more than one policy.
Add-VivaModuleFeaturePolicy -ModuleId VivaPulse -FeatureId PulseExpWithM365Copilot -Name "VivaPulseInM365CopilotEnabled" -IsFeatureEnabled $true -GroupIds "0c8002ac-502a-4228-8545-a5193699b345"
The result is as expected. Now you have to wait 24 hours.
If non-group members with a Microsoft 365 Copilot license open Viva Pulse, they can no longer create new Pulse requests but can respond.
If you do the check, you will find both policies (and all other Viva feature access management policies) in the M365 admin center.