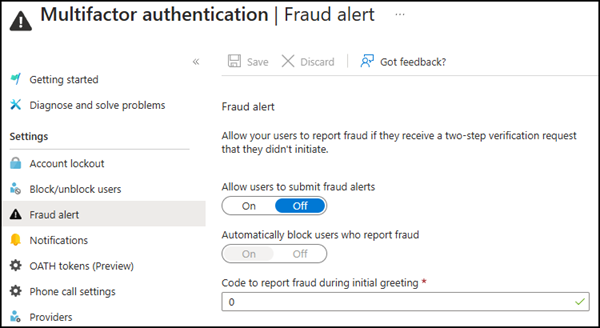
Beginning 1 March 2025, the Fraud Alert feature in Microsoft Entra will be retired in favor of the Report Suspicious Activity feature. This change aims to enhance security by providing deeper integration with Entra ID Protection.
What is changing?
Currently, Microsoft Entra MFA Fraud Alert allows end users to report fraudulent MFA voice calls and Microsoft Authenticator push notifications that they did not initiate. However, starting 1 March 2025, this feature will be retired and replaced with Report Suspicious Activity.
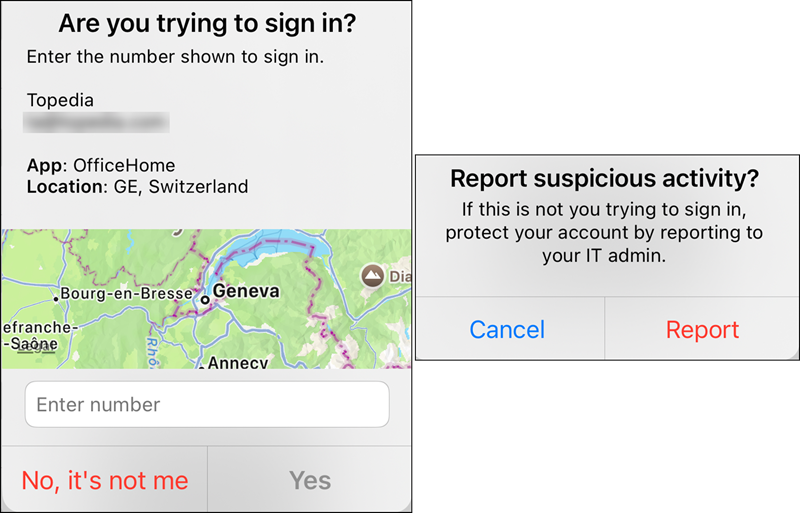
Report Suspicious Activity allows users to flag unauthorized authentication attempts, similar to the existing Fraud Alert feature, but with additional security benefits:
- Deeper integration with Entra ID Protection – The reported activity will be analyzed within Microsoft’s Identity Protection, enabling better remediation.
- Improved fraud detection – The feature ensures that reported suspicious authentication attempts are acted upon more efficiently.
- Better coverage across organizations – Organizations can manage reported activity based on their Microsoft Entra licensing, ensuring that security measures align with their specific needs.
The documentation states that “Report Suspicious Activity” is a feature of Entra ID Protection, which requires Entra ID P2 licensing to use protection through risk-based Conditional Access policies. However, accounts with Entra ID P1 licensing can also use this feature, although they won’t have proactive risk-based policies.
Accounts with Entra ID P1 license
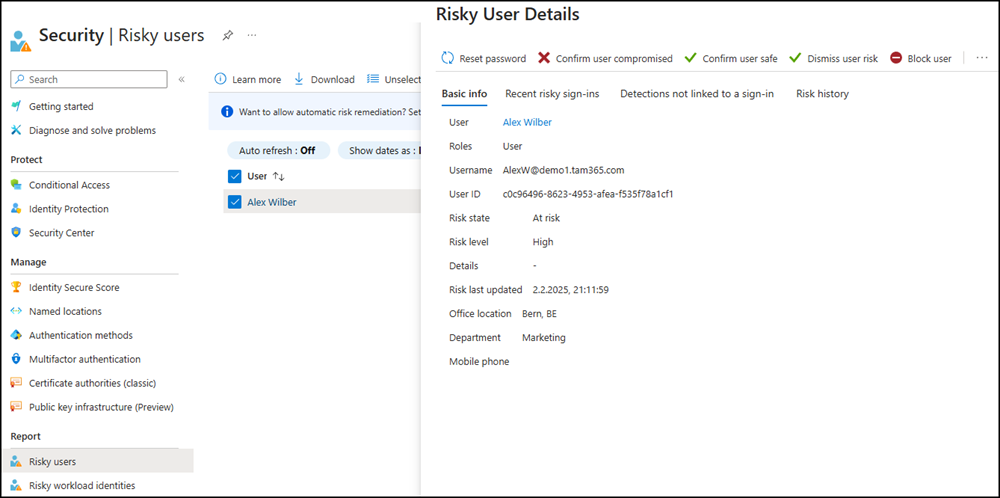
When a user reports an MFA prompt as suspicious, the event shows up in the sign-in logs (as a sign-in that was rejected by the user), in the Audit logs, and in the Risk detections report.
Accounts with Entra ID P2 license
Tenants with a Microsoft Entra ID P2 license can use risk-based Conditional Access policies to automatically remediate user risk, in addition to the options Microsoft Entra ID P2 license. Configure a policy that looks at user risk under Conditions > User risk. Look for users where risk = high to either block them from sign in or require them to reset their password.
What organizations should do?
To maintain seamless fraud reporting, organizations using Microsoft Entra MFA should migrate to Report Suspicious Activity before the retirement date. Here are some steps to take:
- Review current MFA Fraud Alert usage – Identify how the current feature is being utilized and what policies are in place. Read more in the documentation about (legacy) Fraud Alerts.
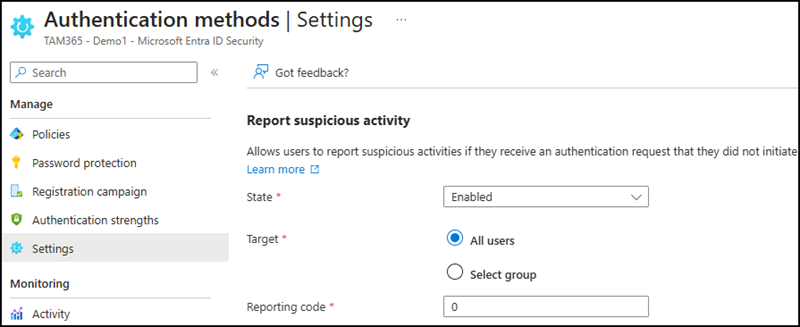
- Enable and communicate the Report Suspicious Activity feature – Ensure that users are educated on how to report suspicious MFA requests through the new feature. Read more in the documentation about how to enable and use Report Suspicious Activity.
This post was automatically generated by my ChatGPT assistant and updated/reviewed manually
