Over the last few weeks, Microsoft has provided regular information about “Microsoft-managed Conditional Access Policies.” The policies are preset by Microsoft with a recommended configuration in the tenant.
Accounts with the Conditional Access Administrator role can manage some policy configurations and activate/deactivate the policies but cannot rename or delete the policies.
A policy has now been created in my tenant: Multifactor authentication for admins accessing Microsoft Admin Portals
This policy covers 14 admin roles that we consider to be highly privileged, who are accessing the Microsoft Admin Portals group, and requires them to perform multifactor authentication. This policy targets Microsoft Entra ID P1 and P2 tenants where security defaults aren’t enabled.
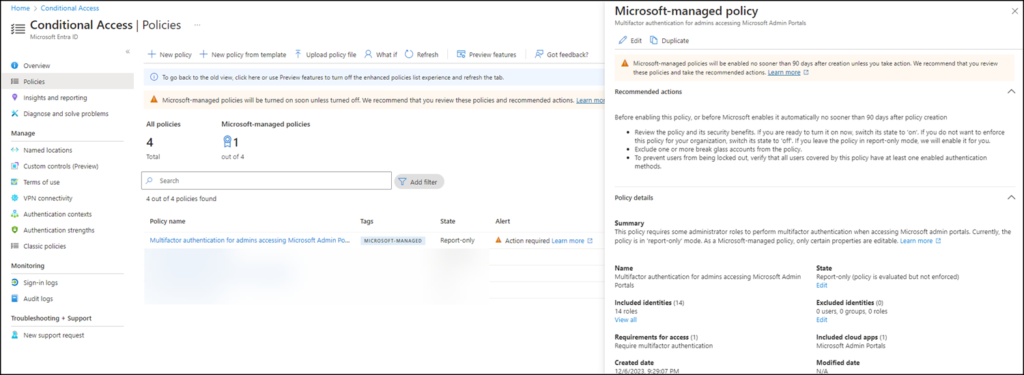
As announced, the policy is in “Report-only” status for 90 days from creation. During this time, administrators can change or deactivate the policy. Microsoft will activate the policy later if the status is not manually disabled within 90 days. In my case, it would be from March 5, 2024.
Other possible policies (depending on the licensing and number of user accounts):
- Multifactor authentication for per-user multifactor authentication users
This policy covers users with per-user MFA, a configuration that Microsoft no longer recommends. These users are targeted by Conditional Access and required to perform multifactor authentication for all cloud apps.
This policy targets Microsoft Entra ID P1 and P2 tenants where security defaults aren’t enabled and there are less than 500 per-user MFA enabled/enforced users.
- Multifactor authentication and reauthentication for risky sign-ins
This policy covers all users and requires MFA and reauthentication when we detect high-risk sign-ins. High-risk in this case means something about the way the user signed in is out of the ordinary. These high-risk sign-ins might include: travel that is highly abnormal, password spray attacks, or token replay attacks. …
This policy targets Microsoft Entra ID P2 tenants where security defaults aren’t enabled and there are enough licenses for each user.
